That's a different service that has nothing to do with the application you're trying to allow.. It sounds like they had you launch a web server (IIS). You can connect since the application is listening on it.
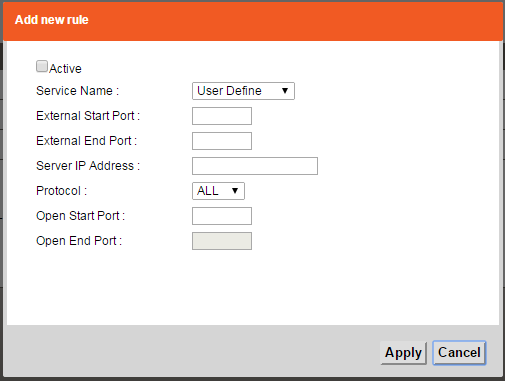
If you really just wanted to test port forwarding anyway you could forward something like external 50000 to internal 80 for that host and then try to have an external/Internet source browse to http://external-ip-here:50000
For a forwarded port it should usually show open if the service is forwarded and listening. If you are filtering by source IP it may show closed or stealth (which you most probably aren't). Usually you will see closed if the service is not listening on that port but the port is forwarded.
What are you even trying to accomplish anyway? Most torrent clients utilize UPnP to begin with. Are your uploads just sucky?
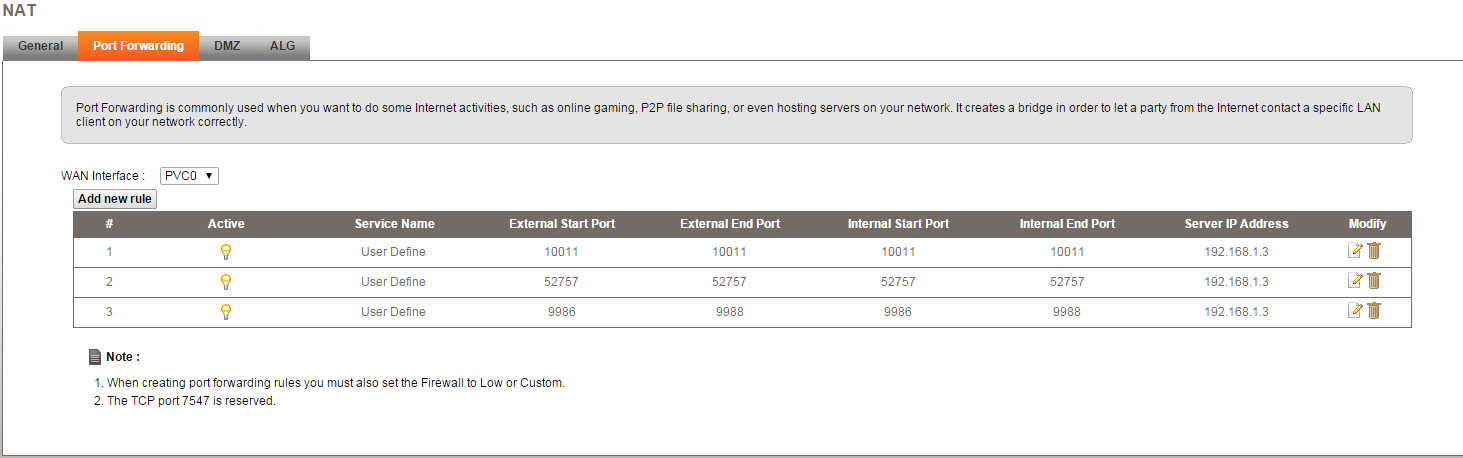
My uploads are pretty god awful, as you mentioned, mostly at 500b/s, but 52757 is just an example that I chose to use for the sake of simplicity. In reality, no port that I forward ever shows as open. For example, I decided to test to see if I could connect to a Teamspeak server hosted on my computer (Which utilises port 9987), and I was unable to connect, as was a third party I requested try and connect. I also occasionally have trouble connecting to users on online games, as I usually have either a closed or moderate NAT. I've also ensured that there's ABSOLUTELY a program listening on the port I am testing.
There's a sticky thread in this sections for my guide: http://www.computerforum.com/232855-how-port-forward.html
It may or may not be helpful if you haven't taken a look already.
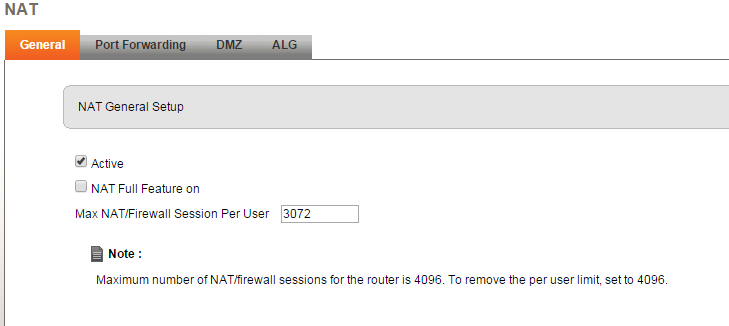
FROM THIS IMAGE YOU HAVE, try to set the port number above and below what you're trying to open. Some routers have issues and won't open the port if the start and end ports are the same.
ISP's can also block forwarding if you're using a router model they own.
Unfortunately, the first thing I did when coming to this forum was check your guide, but I was unable to find a solution within. I've also tried to forward the ports 9986-9988 (Port 9987 is for Teamspeak), but it doesn't appear to have worked, however.
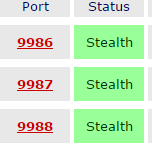
I have a router which is not manufactured by my ISP and is simply a rebranded Zyxel router, but when I checked my ISPs forums their support simply say that they do not "support" port forwarding, and make no mention of actively blocking it.