You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
black screen and more
- Thread starter jjonsalt
- Start date
Malware is on your system most likely. Do the following. Run the rkill program first though.
Please download Malwarebytes' Anti-Malware from here or here and save it to your desktop.
If for some reason Malwarebytes will not install or run please download and run Rkill.scr, Rkill.exe, or Rkill.com. If you are still having issues running rkill then try downloading these renamed versions of the same program.
EXPLORER.EXE
IEXPLORE.EXE
USERINIT.EXE
WINLOGON.EXE
But DO NOT reboot the system and then try installing or running Malwarebytes. If Rkill (which is a black box) appears and then disappears right away or you get a message saying rkill is infected, keep trying to run rkill until it over powers the infection and temporarily kills it. Once a log appears on the screen, you can try running malwarebytes or downloading other programs.
Download the HijackThis installer from here.
Run the installer and choose Install, indicating that you accept the licence agreement. The installer will place a shortcut on your desktop and launch HijackThis.
Click Do a system scan and save a logfile
Most of what HijackThis lists will be harmless or even essential, don't fix anything yet.
When the hijackthis log appears in a notepad file, click on the edit menu, click select all, then click on the edit menu again and click on copy. Come back to your reply and right click on your mouse and click on paste.
Post the logfile that HijackThis produces along with the Malwarebytes Anti-Malware log
Please download Malwarebytes' Anti-Malware from here or here and save it to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to
- Update Malwarebytes' Anti-Malware
- and Launch Malwarebytes' Anti-Malware
- then click Finish.
- If an update is found, it will download and install the latest version. Please keep updating until it says you have the latest version.
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is checked, and click Remove Selected.
- A log will be saved automatically which you can access by clicking on the Logs tab within Malwarebytes' Anti-Malware
If for some reason Malwarebytes will not install or run please download and run Rkill.scr, Rkill.exe, or Rkill.com. If you are still having issues running rkill then try downloading these renamed versions of the same program.
EXPLORER.EXE
IEXPLORE.EXE
USERINIT.EXE
WINLOGON.EXE
But DO NOT reboot the system and then try installing or running Malwarebytes. If Rkill (which is a black box) appears and then disappears right away or you get a message saying rkill is infected, keep trying to run rkill until it over powers the infection and temporarily kills it. Once a log appears on the screen, you can try running malwarebytes or downloading other programs.
Download the HijackThis installer from here.
Run the installer and choose Install, indicating that you accept the licence agreement. The installer will place a shortcut on your desktop and launch HijackThis.
Click Do a system scan and save a logfile
Most of what HijackThis lists will be harmless or even essential, don't fix anything yet.
When the hijackthis log appears in a notepad file, click on the edit menu, click select all, then click on the edit menu again and click on copy. Come back to your reply and right click on your mouse and click on paste.
Post the logfile that HijackThis produces along with the Malwarebytes Anti-Malware log
Go ahead and reboot your system and then post the logs. Open malwarebytes, click on the logs tab and find the log and open it, then copy and paste it back here with the hijackthis log. In order to run hijackthis correctly, you will need to right click on the icon on your desktop and click on run as. If the run as option doesn't appear, then press and hold the shift key while right clicking on the icon.
Malwarebytes' Anti-Malware 1.51.0.1200
www.malwarebytes.org
Database version: 6847
Windows 6.0.6002 Service Pack 2
Internet Explorer 8.0.6001.19048
6/13/2011 9:55:37 AM
mbam-log-2011-06-13 (09-55-37).txt
Scan type: Quick scan
Objects scanned: 193278
Time elapsed: 12 minute(s), 34 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 1
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 8
Memory Processes Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> 5088 -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\773539762 (Trojan.Agent) -> Value: 773539762 -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\1036751.uninstall\uninstall.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\icreinstall\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Windows\Temp\msi3043.tmp (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\0.7269486611895909.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\msiexec.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup(2).exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
---------------------------------------
Malwarebytes' Anti-Malware 1.51.0.1200
www.malwarebytes.org
Database version: 6847
Windows 6.0.6002 Service Pack 2
Internet Explorer 8.0.6001.19048
6/13/2011 9:55:37 AM
mbam-log-2011-06-13 (09-55-37).txt
Scan type: Quick scan
Objects scanned: 193278
Time elapsed: 12 minute(s), 34 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 1
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 8
Memory Processes Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> 5088 -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\773539762 (Trojan.Agent) -> Value: 773539762 -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\1036751.uninstall\uninstall.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\icreinstall\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Windows\Temp\msi3043.tmp (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\0.7269486611895909.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\msiexec.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup(2).exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
www.malwarebytes.org
Database version: 6847
Windows 6.0.6002 Service Pack 2
Internet Explorer 8.0.6001.19048
6/13/2011 9:55:37 AM
mbam-log-2011-06-13 (09-55-37).txt
Scan type: Quick scan
Objects scanned: 193278
Time elapsed: 12 minute(s), 34 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 1
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 8
Memory Processes Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> 5088 -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\773539762 (Trojan.Agent) -> Value: 773539762 -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\1036751.uninstall\uninstall.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\icreinstall\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Windows\Temp\msi3043.tmp (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\0.7269486611895909.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\msiexec.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup(2).exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
---------------------------------------
Malwarebytes' Anti-Malware 1.51.0.1200
www.malwarebytes.org
Database version: 6847
Windows 6.0.6002 Service Pack 2
Internet Explorer 8.0.6001.19048
6/13/2011 9:55:37 AM
mbam-log-2011-06-13 (09-55-37).txt
Scan type: Quick scan
Objects scanned: 193278
Time elapsed: 12 minute(s), 34 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 1
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 8
Memory Processes Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> 5088 -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\773539762 (Trojan.Agent) -> Value: 773539762 -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\1036751.uninstall\uninstall.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\icreinstall\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Windows\Temp\msi3043.tmp (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\0.7269486611895909.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\msiexec.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup(2).exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
Malwarebytes' Anti-Malware 1.51.0.1200
www.malwarebytes.org
Database version: 6847
Windows 6.0.6002 Service Pack 2
Internet Explorer 8.0.6001.19048
6/13/2011 9:55:37 AM
mbam-log-2011-06-13 (09-55-37).txt
Scan type: Quick scan
Objects scanned: 193278
Time elapsed: 12 minute(s), 34 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 1
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 8
Memory Processes Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> 5088 -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\773539762 (Trojan.Agent) -> Value: 773539762 -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\1036751.uninstall\uninstall.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\icreinstall\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Windows\Temp\msi3043.tmp (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\0.7269486611895909.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\msiexec.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup(2).exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
---------------------------------------
Malwarebytes' Anti-Malware 1.51.0.1200
www.malwarebytes.org
Database version: 6847
Windows 6.0.6002 Service Pack 2
Internet Explorer 8.0.6001.19048
6/13/2011 9:55:37 AM
mbam-log-2011-06-13 (09-55-37).txt
Scan type: Quick scan
Objects scanned: 193278
Time elapsed: 12 minute(s), 34 second(s)
Memory Processes Infected: 1
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 1
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 8
Memory Processes Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> 5088 -> Unloaded process successfully.
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\773539762 (Trojan.Agent) -> Value: 773539762 -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Craig\0.46079239188784615.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\1036751.uninstall\uninstall.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\AppData\Local\Temp\icreinstall\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Windows\Temp\msi3043.tmp (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\0.7269486611895909.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\msiexec.exe (Trojan.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup(2).exe (Adware.Agent) -> Quarantined and deleted successfully.
c:\Users\Craig\downloads\videoconvertersetup.exe (Adware.Agent) -> Quarantined and deleted successfully.
Wrong log. I said I needed the second log which is dated 4-1-2012 not the one dated 6-12-2011. Please repost the correct log and do a hijackthis log.
Malwarebytes Anti-Malware 1.60.1.1000
www.malwarebytes.org
Database version: v2012.04.01.01
Windows Vista Service Pack 2 x64 NTFS
Internet Explorer 9.0.8112.16421
Craig :: CRAIG-PC [administrator]
4/1/2012 12:53:12 AM
mbam-log-2012-04-01 (00-53-12).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 229335
Time elapsed: 14 minute(s), 5 second(s)
Memory Processes Detected: 1
C:\ProgramData\hLYMJaTKpxBE.exe (Trojan.Fakealert) -> 5400 -> Delete on reboot.
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 1
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|hLYMJaTKpxBE.exe (Trojan.Fakealert) -> Data: C:\ProgramData\hLYMJaTKpxBE.exe -> Quarantined and deleted successfully.
Registry Data Items Detected: 2
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowMyComputer (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowSearch (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
Folders Detected: 0
(No malicious items detected)
Files Detected: 2
C:\ProgramData\hLYMJaTKpxBE.exe (Trojan.Fakealert) -> Delete on reboot.
C:\Users\Craig\AppData\Local\Temp\V1RvaXTiKfpTvL.exe.tmp (Trojan.Fakealert) -> Quarantined and deleted successfully.
(end)
--------------
I know you don't want screen shots but if the pictured log is what you want it will not let me copy.
www.malwarebytes.org
Database version: v2012.04.01.01
Windows Vista Service Pack 2 x64 NTFS
Internet Explorer 9.0.8112.16421
Craig :: CRAIG-PC [administrator]
4/1/2012 12:53:12 AM
mbam-log-2012-04-01 (00-53-12).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 229335
Time elapsed: 14 minute(s), 5 second(s)
Memory Processes Detected: 1
C:\ProgramData\hLYMJaTKpxBE.exe (Trojan.Fakealert) -> 5400 -> Delete on reboot.
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 1
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|hLYMJaTKpxBE.exe (Trojan.Fakealert) -> Data: C:\ProgramData\hLYMJaTKpxBE.exe -> Quarantined and deleted successfully.
Registry Data Items Detected: 2
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowMyComputer (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowSearch (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
Folders Detected: 0
(No malicious items detected)
Files Detected: 2
C:\ProgramData\hLYMJaTKpxBE.exe (Trojan.Fakealert) -> Delete on reboot.
C:\Users\Craig\AppData\Local\Temp\V1RvaXTiKfpTvL.exe.tmp (Trojan.Fakealert) -> Quarantined and deleted successfully.
(end)
--------------
I know you don't want screen shots but if the pictured log is what you want it will not let me copy.
Last edited:
All fine now?
Not yet, I use my computer for years and now this happens. I thought my VIPRE program would stop these things from happening.
I did as you said-scan with log. I got a blank notepad with the "For so reason..." box. I did the "start, Run, and type" and ended up with the Notepad "The system cannot..." box. Since I use Vista 64 I right clicked on the icon but "Run as administrator" does not appear.
Last edited:
Go ahead and reboot your system and then post the logs. Open malwarebytes, click on the logs tab and find the log and open it, then copy and paste it back here with the hijackthis log. In order to run hijackthis correctly, you will need to right click on the icon on your desktop and click on run as. If the run as option doesn't appear, then press and hold the shift key while right clicking on the icon.
I already stated in one of my earlier posts that if the run as option doesn't appear then press and hold the shift key while right clicking on the icon. Look in my quote above.
Sorry for the problems of pilot error on my part (old age is a bitch) but I think this is what you want.
Logfile of Trend Micro HijackThis v2.0.4
Scan saved at 9:57:53 AM, on 4/2/2012
Platform: Windows Vista SP2 (WinNT 6.00.1906)
MSIE: Internet Explorer v9.00 (9.00.8112.16421)
Boot mode: Normal
Running processes:
C:\Program Files (x86)\Common Files\Dell\apache\bin\httpd.exe
C:\Program Files (x86)\Intel\Intel Matrix Storage Manager\IAAnotif.exe
C:\Program Files (x86)\W3i\InstallIQUpdater\InstallIQUpdater.exe
C:\Program Files (x86)\Panasonic\PHOTOfunSTUDIO -viewer-\PhAutoRun.exe
C:\Program Files (x86)\HP\hpcoretech\hpcmpmgr.exe
C:\Program Files (x86)\Hewlett-Packard\HP Software Update\hpwuSchd.exe
C:\Windows\SysWOW64\hphmon05.exe
C:\Program Files (x86)\Dell Support Center\bin\sprtcmd.exe
C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe
C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe
C:\Program Files (x86)\Real\RealPlayer\Update\realsched.exe
C:\Program Files (x86)\GFI Software\VIPRE\SBAMTray.exe
C:\Program Files (x86)\Mozilla Firefox\firefox.exe
C:\Program Files (x86)\Mozilla Firefox\plugin-container.exe
C:\PROGRA~2\Java\jre6\bin\jp2launcher.exe
C:\Program Files (x86)\Java\jre6\bin\java.exe
C:\Windows\SysWOW64\cmd.exe
C:\Users\Craig\AppData\Local\Akamai\netsession_win.exe
C:\Users\Craig\AppData\Local\Akamai\netsession_win.exe
C:\Program Files (x86)\Broderbund\Screen Shot Standard 8\SSstd8.exe
C:\Program Files (x86)\Trend Micro\HiJackThis\HiJackThis.exe
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://g.msn.com/USCON/1
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://cnn.com/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://g.msn.com/USCON/1
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R0 - HKLM\Software\Microsoft\Internet Explorer\Search,SearchAssistant =
R0 - HKLM\Software\Microsoft\Internet Explorer\Search,CustomizeSearch =
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Local Page = C:\Windows\SysWOW64\blank.htm
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Window Title = Internet Explorer provided by Dell
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = *.local;<local>;127.0.0.1:9421;
R0 - HKCU\Software\Microsoft\Internet Explorer\Toolbar,LinksFolderName =
F2 - REG:system.ini: UserInit=userinit.exe,
O1 - Hosts: ::1 localhost
O2 - BHO: AcroIEHelperStub - {18DF081C-E8AD-4283-A596-FA578C2EBDC3} - C:\Program Files (x86)\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll
O2 - BHO: McAfee Phishing Filter - {27B4851A-3207-45A2-B947-BE8AFE6163AB} - c:\progra~1\mcafee\msk\mskapbho.dll
O2 - BHO: RealPlayer Download and Record Plugin for Internet Explorer - {3049C3E9-B461-4BC5-8870-4C09146192CA} - C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\IE\rpbrowserrecordplugin.dll
O2 - BHO: Canon Easy-WebPrint EX BHO - {3785D0AD-BFFF-47F6-BF5B-A587C162FED9} - C:\Program Files (x86)\Canon\Easy-WebPrint EX\ewpexbho.dll
O2 - BHO: (no name) - {5C255C8A-E604-49b4-9D64-90988571CECB} - (no file)
O2 - BHO: PhotoPos Toolbar - {5D0EC45B-D2E4-4DD0-A5B2-69DDEFE852A8} - C:\Program Files (x86)\PhotoposComTbr\PhotoposComTbrLib.dll
O2 - BHO: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\PROGRA~2\MICROS~2\Office14\GROOVEEX.DLL
O2 - BHO: scriptproxy - {7DB2D5A0-7241-4E79-B68D-6309F01C5231} - C:\Program Files (x86)\Common Files\McAfee\SystemCore\ScriptSn.20100916033019.dll
O2 - BHO: Windows Live Sign-in Helper - {9030D464-4C02-4ABF-8ECC-5164760863C6} - C:\Program Files (x86)\Common Files\Microsoft Shared\Windows Live\WindowsLiveLogin.dll
O2 - BHO: URLRedirectionBHO - {B4F3A835-0E21-4959-BA22-42B3008E02FF} - C:\PROGRA~2\MICROS~2\Office14\URLREDIR.DLL
O2 - BHO: IEHlprObjClass - {CE7C3CF0-4B15-11D1-ABED-709549C10000} - C:\Program Files (x86)\Kensington\MouseWorks\IE_SPY.DLL (file missing)
O2 - BHO: Bing Bar Helper - {d2ce3e00-f94a-4740-988e-03dc2f38c34f} - "C:\Program Files (x86)\Microsoft\BingBar\BingExt.dll" (file missing)
O2 - BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files (x86)\Java\jre6\bin\jp2ssv.dll
O3 - Toolbar: Canon Easy-WebPrint EX - {759D9886-0C6F-4498-BAB6-4A5F47C6C72F} - C:\Program Files (x86)\Canon\Easy-WebPrint EX\ewpexhlp.dll
O3 - Toolbar: PhotoPos Toolbar - {5D0EC45B-D2E4-4DD0-A5B2-69DDEFE852A8} - C:\Program Files (x86)\PhotoposComTbr\PhotoposComTbrLib.dll
O3 - Toolbar: Bing Bar - {8dcb7100-df86-4384-8842-8fa844297b3f} - "C:\Program Files (x86)\Microsoft\BingBar\BingExt.dll" (file missing)
O4 - HKLM\..\Run: [HPHUPD05] C:\Program Files (x86)\Hewlett-Packard\{45B6180B-DCAB-4093-8EE8-6164457517F0}\hphupd05.exe
O4 - HKLM\..\Run: [HP Component Manager] "C:\Program Files (x86)\HP\hpcoretech\hpcmpmgr.exe"
O4 - HKLM\..\Run: [HP Software Update] "C:\Program Files (x86)\Hewlett-Packard\HP Software Update\HPWuSchd.exe"
O4 - HKLM\..\Run: [HPHmon05] C:\Windows\SysWOW64\hphmon05.exe
O4 - HKLM\..\Run: [dellsupportcenter] "C:\Program Files (x86)\Dell Support Center\bin\sprtcmd.exe" /P dellsupportcenter
O4 - HKLM\..\Run: [QuickFinder Scheduler] "c:\Program Files (x86)\Corel\WordPerfect Office X4\Programs\QFSCHD140.EXE"
O4 - HKLM\..\Run: [StartCCC] "C:\Program Files (x86)\ATI Technologies\ATI.ACE\Core-Static\CLIStart.exe" MSRun
O4 - HKLM\..\Run: [ATICustomerCare] "C:\Program Files (x86)\ATI\ATICustomerCare\ATICustomerCare.exe"
O4 - HKLM\..\Run: [mcui_exe] "C:\Program Files\McAfee.com\Agent\mcagent.exe" /runkey
O4 - HKLM\..\Run: [SwitchBoard] "C:\Program Files (x86)\Common Files\Adobe\SwitchBoard\SwitchBoard.exe"
O4 - HKLM\..\Run: [AdobeCS5ServiceManager] "C:\Program Files (x86)\Common Files\Adobe\CS5ServiceManager\CS5ServiceManager.exe" -launchedbylogin
O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Program Files (x86)\Adobe\Reader 9.0\Reader\Reader_sl.exe"
O4 - HKLM\..\Run: [Adobe ARM] "C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe"
O4 - HKLM\..\Run: [ArcSoft Connection Service] "C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe"
O4 - HKLM\..\Run: [BCSSync] "C:\Program Files (x86)\Microsoft Office\Office14\BCSSync.exe" /DelayServices
O4 - HKLM\..\Run: [TkBellExe] "c:\program files (x86)\real\realplayer\Update\realsched.exe" -osboot
O4 - HKLM\..\Run: [SBAMTray] "C:\Program Files (x86)\GFI Software\VIPRE\SBAMTray.exe"
O4 - HKCU\..\Run: [ehTray.exe] C:\Windows\ehome\ehTray.exe
O4 - HKCU\..\Run: [WMPNSCFG] C:\Program Files (x86)\Windows Media Player\WMPNSCFG.exe
O4 - HKCU\..\Run: [InstallIQUpdater] "C:\Program Files (x86)\W3i\InstallIQUpdater\InstallIQUpdater.exe" /silent /autorun
O4 - HKCU\..\Run: [Akamai NetSession Interface] "C:\Users\Craig\AppData\Local\Akamai\netsession_win.exe"
O4 - HKUS\S-1-5-19\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User 'LOCAL SERVICE')
O4 - HKUS\S-1-5-19\..\Run: [WindowsWelcomeCenter] rundll32.exe oobefldr.dll,ShowWelcomeCenter (User 'LOCAL SERVICE')
O4 - HKUS\S-1-5-20\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User 'NETWORK SERVICE')
O4 - HKUS\S-1-5-21-331170553-3217227580-529626252-1001\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User 'RA Media Server')
O4 - HKUS\S-1-5-18\..\Run: [20090604] C:\Program Files (x86)\WillWriter\registration\encore_reg.exe /r "C:\Program Files (x86)\WillWriter\registration\encore_reg.rpd" (User 'SYSTEM')
O4 - HKUS\.DEFAULT\..\Run: [20090604] C:\Program Files (x86)\WillWriter\registration\encore_reg.exe /r "C:\Program Files (x86)\WillWriter\registration\encore_reg.rpd" (User 'Default user')
O4 - Global Startup: Event Reminder.lnk = C:\Program Files (x86)\The Print Shop 23\Remind.exe
O4 - Global Startup: PHOTOfunSTUDIO -viewer-.lnk = C:\Program Files (x86)\Panasonic\PHOTOfunSTUDIO -viewer-\PhAutoRun.exe
O8 - Extra context menu item: Add to Google Photos Screensa&ver - res://C:\Windows\system32\GPhotos.scr/200
O8 - Extra context menu item: Copy to &Lightning Note - c:\Program Files (x86)\Corel\WordPerfect Lightning\Programs\WPLightningCopyToNote.hta
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~2\MICROS~2\Office14\EXCEL.EXE/3000
O8 - Extra context menu item: Open with WordPerfect - c:\Program Files (x86)\Corel\WordPerfect Office X4\Programs\WPLauncher.hta
O8 - Extra context menu item: Se&nd to OneNote - res://C:\PROGRA~2\MICROS~2\Office14\ONBttnIE.dll/105
O8 - Extra context menu item: Send image to &Bluetooth Device... - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie_ctx.htm
O8 - Extra context menu item: Send page to &Bluetooth Device... - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie.htm
O9 - Extra button: Blog This - {219C3416-8CB2-491a-A3C7-D9FCDDC9D600} - C:\Program Files (x86)\Windows Live\Writer\WriterBrowserExtension.dll
O9 - Extra 'Tools' menuitem: &Blog This in Windows Live Writer - {219C3416-8CB2-491a-A3C7-D9FCDDC9D600} - C:\Program Files (x86)\Windows Live\Writer\WriterBrowserExtension.dll
O9 - Extra button: Send to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIE.dll
O9 - Extra 'Tools' menuitem: Se&nd to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIE.dll
O9 - Extra button: OneNote Lin&ked Notes - {789FE86F-6FC4-46A1-9849-EDE0DB0C95CA} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIELinkedNotes.dll
O9 - Extra 'Tools' menuitem: OneNote Lin&ked Notes - {789FE86F-6FC4-46A1-9849-EDE0DB0C95CA} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIELinkedNotes.dll
O9 - Extra button: Send To Bluetooth - {CCA281CA-C863-46ef-9331-5C8D4460577F} - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie.htm
O9 - Extra 'Tools' menuitem: Send to &Bluetooth Device... - {CCA281CA-C863-46ef-9331-5C8D4460577F} - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie.htm
O11 - Options group: [ACCELERATED_GRAPHICS] Accelerated graphics
O15 - Trusted Zone: http://*.mcafee.com
O18 - Filter hijack: text/xml - {807573E5-5146-11D5-A672-00B0D022E945} - C:\Program Files (x86)\Common Files\Microsoft Shared\OFFICE14\MSOXMLMF.DLL
O22 - SharedTaskScheduler: Component Categories cache daemon - {8C7461EF-2B13-11d2-BE35-3078302C2030} - C:\Windows\system32\browseui.dll
O23 - Service: ArcSoft Connect Daemon (ACDaemon) - ArcSoft - C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe
O23 - Service: Andrea RT Filters Service (AERTFilters) - Andrea Electronics Corporation - C:\Program Files\Realtek\Audio\HDA\AERTSr64.exe
O23 - Service: @%SystemRoot%\system32\Alg.exe,-112 (ALG) - Unknown owner - C:\Windows\System32\alg.exe (file missing)
O23 - Service: AMD External Events Utility - Unknown owner - C:\Windows\system32\atiesrxx.exe (file missing)
O23 - Service: Remote Access Media Server (Apache2.2) - Apache Software Foundation - C:\Program Files (x86)\Common Files\Dell\apache\bin\httpd.exe
O23 - Service: ASP.NET State Service (aspnet_state) - Unknown owner - C:\Windows\Microsoft.NET\Framework\v2.0.50727\aspnet_state.exe (file missing)
O23 - Service: ##Id_String1.6844F930_1628_4223_B5CC_5BB94B879762## (Bonjour Service) - Apple Computer, Inc. - C:\Program Files (x86)\Bonjour\mDNSResponder.exe
O23 - Service: Canon Camera Access Library 8 (CCALib8) - Canon Inc. - C:\Program Files (x86)\Canon\CAL\CALMAIN.exe
O23 - Service: Creative ALchemy AL6 Licensing Service - Creative Labs - C:\Program Files (x86)\Common Files\Creative Labs Shared\Service\AL6Licensing.exe
O23 - Service: Creative Audio Engine Licensing Service - Creative Labs - C:\Program Files (x86)\Common Files\Creative Labs Shared\Service\CTAELicensing.exe
O23 - Service: Creative Audio Service (CTAudSvcService) - Creative Technology Ltd - C:\Program Files (x86)\Creative\Shared Files\CTAudSvc.exe
O23 - Service: @dfsrres.dll,-101 (DFSR) - Unknown owner - C:\Windows\system32\DFSR.exe (file missing)
O23 - Service: Remote Access DB (dsl-db) - Unknown owner - C:\Program Files (x86)\Common Files\Dell\MySQL\bin\mysqld.exe
O23 - Service: Remote Access File Sync Service (dsl-fs-sync) - SingleClick Systems - C:\Program Files (x86)\Common Files\Dell\Remote Access File Sync Service\dsl_fs_sync.exe
O23 - Service: FLEXnet Licensing Service - Acresso Software Inc. - C:\Program Files (x86)\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe
O23 - Service: Google Update Service (gupdate) (gupdate) - Google Inc. - C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
O23 - Service: Google Update Service (gupdatem) (gupdatem) - Google Inc. - C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
O23 - Service: Google Updater Service (gusvc) - Google - C:\Program Files (x86)\Google\Common\Google Updater\GoogleUpdaterService.exe
O23 - Service: Advanced Networking Service (hnmsvc) - Dell Inc. - c:\Program Files (x86)\Common Files\Dell\Advanced Networking Service\hnm_svc.exe
O23 - Service: Intel(R) Matrix Storage Event Monitor (IAANTMON) - Intel Corporation - C:\Program Files (x86)\Intel\Intel Matrix Storage Manager\IAANTMon.exe
O23 - Service: iolo FileInfoList Service (ioloFileInfoList) - Unknown owner - C:\Program Files (x86)\iolo\common\lib\ioloServiceManager.exe
O23 - Service: iolo System Service (ioloSystemService) - Unknown owner - C:\Program Files (x86)\iolo\common\lib\ioloServiceManager.exe
O23 - Service: @keyiso.dll,-100 (KeyIso) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: McAfee Personal Firewall Service (McMPFSvc) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee Services (mcmscsvc) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee VirusScan Announcer (McNaiAnn) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee Network Agent (McNASvc) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee Scanner (McODS) - McAfee, Inc. - C:\Program Files\McAfee\VirusScan\mcods.exe
O23 - Service: McAfee Proxy Service (McProxy) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McShield - McAfee, Inc. - C:\Program Files\Common Files\McAfee\SystemCore\\mcshield.exe
O23 - Service: McAfee Firewall Core Service (mfefire) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\SystemCore\\mfefire.exe
O23 - Service: McAfee Validation Trust Protection Service (mfevtp) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\SystemCore\mfevtps.exe
O23 - Service: @comres.dll,-2797 (MSDTC) - Unknown owner - C:\Windows\System32\msdtc.exe (file missing)
O23 - Service: McAfee Anti-Spam Service (MSK80Service) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: @%SystemRoot%\System32\netlogon.dll,-102 (Netlogon) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: @%systemroot%\system32\psbase.dll,-300 (ProtectedStorage) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: Protexis Licensing V2 (PSI_SVC_2) - Protexis Inc. - c:\Program Files (x86)\Common Files\Protexis\License Service\PsiService_2.exe
O23 - Service: @%systemroot%\system32\Locator.exe,-2 (RpcLocator) - Unknown owner - C:\Windows\system32\locator.exe (file missing)
O23 - Service: @%SystemRoot%\system32\samsrv.dll,-1 (SamSs) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: VIPRE Antivirus (SBAMSvc) - GFI Software - C:\Program Files (x86)\GFI Software\VIPRE\SBAMSvc.exe
O23 - Service: SB Recovery Service (SBPIMSvc) - GFI Software - C:\Program Files (x86)\GFI Software\VIPRE\SBPIMSvc.exe
O23 - Service: @%SystemRoot%\system32\SLsvc.exe,-101 (slsvc) - Unknown owner - C:\Windows\system32\SLsvc.exe (file missing)
O23 - Service: @%SystemRoot%\system32\snmptrap.exe,-3 (SNMPTRAP) - Unknown owner - C:\Windows\System32\snmptrap.exe (file missing)
O23 - Service: Sound Blaster X-Fi MB Licensing Service - Creative Labs - C:\Program Files (x86)\Common Files\Creative Labs Shared\Service\XMBLicensing.exe
O23 - Service: @%systemroot%\system32\spoolsv.exe,-1 (Spooler) - Unknown owner - C:\Windows\System32\spoolsv.exe (file missing)
O23 - Service: SupportSoft Sprocket Service (DellSupportCenter) (sprtsvc_DellSupportCenter) - SupportSoft, Inc. - C:\Program Files (x86)\Dell Support Center\bin\sprtsvc.exe
O23 - Service: stllssvr - MicroVision Development, Inc. - C:\Program Files (x86)\Common Files\SureThing Shared\stllssvr.exe
O23 - Service: Adobe SwitchBoard (SwitchBoard) - Adobe Systems Incorporated - C:\Program Files (x86)\Common Files\Adobe\SwitchBoard\SwitchBoard.exe
O23 - Service: @%SystemRoot%\system32\ui0detect.exe,-101 (UI0Detect) - Unknown owner - C:\Windows\system32\UI0Detect.exe (file missing)
O23 - Service: @%SystemRoot%\system32\vds.exe,-100 (vds) - Unknown owner - C:\Windows\System32\vds.exe (file missing)
O23 - Service: @%systemroot%\system32\vssvc.exe,-102 (VSS) - Unknown owner - C:\Windows\system32\vssvc.exe (file missing)
O23 - Service: @%Systemroot%\system32\wbem\wmiapsrv.exe,-110 (wmiApSrv) - Unknown owner - C:\Windows\system32\wbem\WmiApSrv.exe (file missing)
O23 - Service: @%ProgramFiles%\Windows Media Player\wmpnetwk.exe,-101 (WMPNetworkSvc) - Unknown owner - C:\Program Files (x86)\Windows Media Player\wmpnetwk.exe (file missing)
--
End of file - 17797 bytes
Logfile of Trend Micro HijackThis v2.0.4
Scan saved at 9:57:53 AM, on 4/2/2012
Platform: Windows Vista SP2 (WinNT 6.00.1906)
MSIE: Internet Explorer v9.00 (9.00.8112.16421)
Boot mode: Normal
Running processes:
C:\Program Files (x86)\Common Files\Dell\apache\bin\httpd.exe
C:\Program Files (x86)\Intel\Intel Matrix Storage Manager\IAAnotif.exe
C:\Program Files (x86)\W3i\InstallIQUpdater\InstallIQUpdater.exe
C:\Program Files (x86)\Panasonic\PHOTOfunSTUDIO -viewer-\PhAutoRun.exe
C:\Program Files (x86)\HP\hpcoretech\hpcmpmgr.exe
C:\Program Files (x86)\Hewlett-Packard\HP Software Update\hpwuSchd.exe
C:\Windows\SysWOW64\hphmon05.exe
C:\Program Files (x86)\Dell Support Center\bin\sprtcmd.exe
C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe
C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe
C:\Program Files (x86)\Real\RealPlayer\Update\realsched.exe
C:\Program Files (x86)\GFI Software\VIPRE\SBAMTray.exe
C:\Program Files (x86)\Mozilla Firefox\firefox.exe
C:\Program Files (x86)\Mozilla Firefox\plugin-container.exe
C:\PROGRA~2\Java\jre6\bin\jp2launcher.exe
C:\Program Files (x86)\Java\jre6\bin\java.exe
C:\Windows\SysWOW64\cmd.exe
C:\Users\Craig\AppData\Local\Akamai\netsession_win.exe
C:\Users\Craig\AppData\Local\Akamai\netsession_win.exe
C:\Program Files (x86)\Broderbund\Screen Shot Standard 8\SSstd8.exe
C:\Program Files (x86)\Trend Micro\HiJackThis\HiJackThis.exe
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://g.msn.com/USCON/1
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://cnn.com/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://g.msn.com/USCON/1
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R0 - HKLM\Software\Microsoft\Internet Explorer\Search,SearchAssistant =
R0 - HKLM\Software\Microsoft\Internet Explorer\Search,CustomizeSearch =
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Local Page = C:\Windows\SysWOW64\blank.htm
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Window Title = Internet Explorer provided by Dell
R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = *.local;<local>;127.0.0.1:9421;
R0 - HKCU\Software\Microsoft\Internet Explorer\Toolbar,LinksFolderName =
F2 - REG:system.ini: UserInit=userinit.exe,
O1 - Hosts: ::1 localhost
O2 - BHO: AcroIEHelperStub - {18DF081C-E8AD-4283-A596-FA578C2EBDC3} - C:\Program Files (x86)\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll
O2 - BHO: McAfee Phishing Filter - {27B4851A-3207-45A2-B947-BE8AFE6163AB} - c:\progra~1\mcafee\msk\mskapbho.dll
O2 - BHO: RealPlayer Download and Record Plugin for Internet Explorer - {3049C3E9-B461-4BC5-8870-4C09146192CA} - C:\ProgramData\Real\RealPlayer\BrowserRecordPlugin\IE\rpbrowserrecordplugin.dll
O2 - BHO: Canon Easy-WebPrint EX BHO - {3785D0AD-BFFF-47F6-BF5B-A587C162FED9} - C:\Program Files (x86)\Canon\Easy-WebPrint EX\ewpexbho.dll
O2 - BHO: (no name) - {5C255C8A-E604-49b4-9D64-90988571CECB} - (no file)
O2 - BHO: PhotoPos Toolbar - {5D0EC45B-D2E4-4DD0-A5B2-69DDEFE852A8} - C:\Program Files (x86)\PhotoposComTbr\PhotoposComTbrLib.dll
O2 - BHO: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\PROGRA~2\MICROS~2\Office14\GROOVEEX.DLL
O2 - BHO: scriptproxy - {7DB2D5A0-7241-4E79-B68D-6309F01C5231} - C:\Program Files (x86)\Common Files\McAfee\SystemCore\ScriptSn.20100916033019.dll
O2 - BHO: Windows Live Sign-in Helper - {9030D464-4C02-4ABF-8ECC-5164760863C6} - C:\Program Files (x86)\Common Files\Microsoft Shared\Windows Live\WindowsLiveLogin.dll
O2 - BHO: URLRedirectionBHO - {B4F3A835-0E21-4959-BA22-42B3008E02FF} - C:\PROGRA~2\MICROS~2\Office14\URLREDIR.DLL
O2 - BHO: IEHlprObjClass - {CE7C3CF0-4B15-11D1-ABED-709549C10000} - C:\Program Files (x86)\Kensington\MouseWorks\IE_SPY.DLL (file missing)
O2 - BHO: Bing Bar Helper - {d2ce3e00-f94a-4740-988e-03dc2f38c34f} - "C:\Program Files (x86)\Microsoft\BingBar\BingExt.dll" (file missing)
O2 - BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files (x86)\Java\jre6\bin\jp2ssv.dll
O3 - Toolbar: Canon Easy-WebPrint EX - {759D9886-0C6F-4498-BAB6-4A5F47C6C72F} - C:\Program Files (x86)\Canon\Easy-WebPrint EX\ewpexhlp.dll
O3 - Toolbar: PhotoPos Toolbar - {5D0EC45B-D2E4-4DD0-A5B2-69DDEFE852A8} - C:\Program Files (x86)\PhotoposComTbr\PhotoposComTbrLib.dll
O3 - Toolbar: Bing Bar - {8dcb7100-df86-4384-8842-8fa844297b3f} - "C:\Program Files (x86)\Microsoft\BingBar\BingExt.dll" (file missing)
O4 - HKLM\..\Run: [HPHUPD05] C:\Program Files (x86)\Hewlett-Packard\{45B6180B-DCAB-4093-8EE8-6164457517F0}\hphupd05.exe
O4 - HKLM\..\Run: [HP Component Manager] "C:\Program Files (x86)\HP\hpcoretech\hpcmpmgr.exe"
O4 - HKLM\..\Run: [HP Software Update] "C:\Program Files (x86)\Hewlett-Packard\HP Software Update\HPWuSchd.exe"
O4 - HKLM\..\Run: [HPHmon05] C:\Windows\SysWOW64\hphmon05.exe
O4 - HKLM\..\Run: [dellsupportcenter] "C:\Program Files (x86)\Dell Support Center\bin\sprtcmd.exe" /P dellsupportcenter
O4 - HKLM\..\Run: [QuickFinder Scheduler] "c:\Program Files (x86)\Corel\WordPerfect Office X4\Programs\QFSCHD140.EXE"
O4 - HKLM\..\Run: [StartCCC] "C:\Program Files (x86)\ATI Technologies\ATI.ACE\Core-Static\CLIStart.exe" MSRun
O4 - HKLM\..\Run: [ATICustomerCare] "C:\Program Files (x86)\ATI\ATICustomerCare\ATICustomerCare.exe"
O4 - HKLM\..\Run: [mcui_exe] "C:\Program Files\McAfee.com\Agent\mcagent.exe" /runkey
O4 - HKLM\..\Run: [SwitchBoard] "C:\Program Files (x86)\Common Files\Adobe\SwitchBoard\SwitchBoard.exe"
O4 - HKLM\..\Run: [AdobeCS5ServiceManager] "C:\Program Files (x86)\Common Files\Adobe\CS5ServiceManager\CS5ServiceManager.exe" -launchedbylogin
O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Program Files (x86)\Adobe\Reader 9.0\Reader\Reader_sl.exe"
O4 - HKLM\..\Run: [Adobe ARM] "C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe"
O4 - HKLM\..\Run: [ArcSoft Connection Service] "C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe"
O4 - HKLM\..\Run: [BCSSync] "C:\Program Files (x86)\Microsoft Office\Office14\BCSSync.exe" /DelayServices
O4 - HKLM\..\Run: [TkBellExe] "c:\program files (x86)\real\realplayer\Update\realsched.exe" -osboot
O4 - HKLM\..\Run: [SBAMTray] "C:\Program Files (x86)\GFI Software\VIPRE\SBAMTray.exe"
O4 - HKCU\..\Run: [ehTray.exe] C:\Windows\ehome\ehTray.exe
O4 - HKCU\..\Run: [WMPNSCFG] C:\Program Files (x86)\Windows Media Player\WMPNSCFG.exe
O4 - HKCU\..\Run: [InstallIQUpdater] "C:\Program Files (x86)\W3i\InstallIQUpdater\InstallIQUpdater.exe" /silent /autorun
O4 - HKCU\..\Run: [Akamai NetSession Interface] "C:\Users\Craig\AppData\Local\Akamai\netsession_win.exe"
O4 - HKUS\S-1-5-19\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User 'LOCAL SERVICE')
O4 - HKUS\S-1-5-19\..\Run: [WindowsWelcomeCenter] rundll32.exe oobefldr.dll,ShowWelcomeCenter (User 'LOCAL SERVICE')
O4 - HKUS\S-1-5-20\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User 'NETWORK SERVICE')
O4 - HKUS\S-1-5-21-331170553-3217227580-529626252-1001\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User 'RA Media Server')
O4 - HKUS\S-1-5-18\..\Run: [20090604] C:\Program Files (x86)\WillWriter\registration\encore_reg.exe /r "C:\Program Files (x86)\WillWriter\registration\encore_reg.rpd" (User 'SYSTEM')
O4 - HKUS\.DEFAULT\..\Run: [20090604] C:\Program Files (x86)\WillWriter\registration\encore_reg.exe /r "C:\Program Files (x86)\WillWriter\registration\encore_reg.rpd" (User 'Default user')
O4 - Global Startup: Event Reminder.lnk = C:\Program Files (x86)\The Print Shop 23\Remind.exe
O4 - Global Startup: PHOTOfunSTUDIO -viewer-.lnk = C:\Program Files (x86)\Panasonic\PHOTOfunSTUDIO -viewer-\PhAutoRun.exe
O8 - Extra context menu item: Add to Google Photos Screensa&ver - res://C:\Windows\system32\GPhotos.scr/200
O8 - Extra context menu item: Copy to &Lightning Note - c:\Program Files (x86)\Corel\WordPerfect Lightning\Programs\WPLightningCopyToNote.hta
O8 - Extra context menu item: E&xport to Microsoft Excel - res://C:\PROGRA~2\MICROS~2\Office14\EXCEL.EXE/3000
O8 - Extra context menu item: Open with WordPerfect - c:\Program Files (x86)\Corel\WordPerfect Office X4\Programs\WPLauncher.hta
O8 - Extra context menu item: Se&nd to OneNote - res://C:\PROGRA~2\MICROS~2\Office14\ONBttnIE.dll/105
O8 - Extra context menu item: Send image to &Bluetooth Device... - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie_ctx.htm
O8 - Extra context menu item: Send page to &Bluetooth Device... - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie.htm
O9 - Extra button: Blog This - {219C3416-8CB2-491a-A3C7-D9FCDDC9D600} - C:\Program Files (x86)\Windows Live\Writer\WriterBrowserExtension.dll
O9 - Extra 'Tools' menuitem: &Blog This in Windows Live Writer - {219C3416-8CB2-491a-A3C7-D9FCDDC9D600} - C:\Program Files (x86)\Windows Live\Writer\WriterBrowserExtension.dll
O9 - Extra button: Send to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIE.dll
O9 - Extra 'Tools' menuitem: Se&nd to OneNote - {2670000A-7350-4f3c-8081-5663EE0C6C49} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIE.dll
O9 - Extra button: OneNote Lin&ked Notes - {789FE86F-6FC4-46A1-9849-EDE0DB0C95CA} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIELinkedNotes.dll
O9 - Extra 'Tools' menuitem: OneNote Lin&ked Notes - {789FE86F-6FC4-46A1-9849-EDE0DB0C95CA} - C:\Program Files (x86)\Microsoft Office\Office14\ONBttnIELinkedNotes.dll
O9 - Extra button: Send To Bluetooth - {CCA281CA-C863-46ef-9331-5C8D4460577F} - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie.htm
O9 - Extra 'Tools' menuitem: Send to &Bluetooth Device... - {CCA281CA-C863-46ef-9331-5C8D4460577F} - C:\Program Files\WIDCOMM\Bluetooth Software\btsendto_ie.htm
O11 - Options group: [ACCELERATED_GRAPHICS] Accelerated graphics
O15 - Trusted Zone: http://*.mcafee.com
O18 - Filter hijack: text/xml - {807573E5-5146-11D5-A672-00B0D022E945} - C:\Program Files (x86)\Common Files\Microsoft Shared\OFFICE14\MSOXMLMF.DLL
O22 - SharedTaskScheduler: Component Categories cache daemon - {8C7461EF-2B13-11d2-BE35-3078302C2030} - C:\Windows\system32\browseui.dll
O23 - Service: ArcSoft Connect Daemon (ACDaemon) - ArcSoft - C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe
O23 - Service: Andrea RT Filters Service (AERTFilters) - Andrea Electronics Corporation - C:\Program Files\Realtek\Audio\HDA\AERTSr64.exe
O23 - Service: @%SystemRoot%\system32\Alg.exe,-112 (ALG) - Unknown owner - C:\Windows\System32\alg.exe (file missing)
O23 - Service: AMD External Events Utility - Unknown owner - C:\Windows\system32\atiesrxx.exe (file missing)
O23 - Service: Remote Access Media Server (Apache2.2) - Apache Software Foundation - C:\Program Files (x86)\Common Files\Dell\apache\bin\httpd.exe
O23 - Service: ASP.NET State Service (aspnet_state) - Unknown owner - C:\Windows\Microsoft.NET\Framework\v2.0.50727\aspnet_state.exe (file missing)
O23 - Service: ##Id_String1.6844F930_1628_4223_B5CC_5BB94B879762## (Bonjour Service) - Apple Computer, Inc. - C:\Program Files (x86)\Bonjour\mDNSResponder.exe
O23 - Service: Canon Camera Access Library 8 (CCALib8) - Canon Inc. - C:\Program Files (x86)\Canon\CAL\CALMAIN.exe
O23 - Service: Creative ALchemy AL6 Licensing Service - Creative Labs - C:\Program Files (x86)\Common Files\Creative Labs Shared\Service\AL6Licensing.exe
O23 - Service: Creative Audio Engine Licensing Service - Creative Labs - C:\Program Files (x86)\Common Files\Creative Labs Shared\Service\CTAELicensing.exe
O23 - Service: Creative Audio Service (CTAudSvcService) - Creative Technology Ltd - C:\Program Files (x86)\Creative\Shared Files\CTAudSvc.exe
O23 - Service: @dfsrres.dll,-101 (DFSR) - Unknown owner - C:\Windows\system32\DFSR.exe (file missing)
O23 - Service: Remote Access DB (dsl-db) - Unknown owner - C:\Program Files (x86)\Common Files\Dell\MySQL\bin\mysqld.exe
O23 - Service: Remote Access File Sync Service (dsl-fs-sync) - SingleClick Systems - C:\Program Files (x86)\Common Files\Dell\Remote Access File Sync Service\dsl_fs_sync.exe
O23 - Service: FLEXnet Licensing Service - Acresso Software Inc. - C:\Program Files (x86)\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe
O23 - Service: Google Update Service (gupdate) (gupdate) - Google Inc. - C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
O23 - Service: Google Update Service (gupdatem) (gupdatem) - Google Inc. - C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
O23 - Service: Google Updater Service (gusvc) - Google - C:\Program Files (x86)\Google\Common\Google Updater\GoogleUpdaterService.exe
O23 - Service: Advanced Networking Service (hnmsvc) - Dell Inc. - c:\Program Files (x86)\Common Files\Dell\Advanced Networking Service\hnm_svc.exe
O23 - Service: Intel(R) Matrix Storage Event Monitor (IAANTMON) - Intel Corporation - C:\Program Files (x86)\Intel\Intel Matrix Storage Manager\IAANTMon.exe
O23 - Service: iolo FileInfoList Service (ioloFileInfoList) - Unknown owner - C:\Program Files (x86)\iolo\common\lib\ioloServiceManager.exe
O23 - Service: iolo System Service (ioloSystemService) - Unknown owner - C:\Program Files (x86)\iolo\common\lib\ioloServiceManager.exe
O23 - Service: @keyiso.dll,-100 (KeyIso) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: McAfee Personal Firewall Service (McMPFSvc) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee Services (mcmscsvc) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee VirusScan Announcer (McNaiAnn) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee Network Agent (McNASvc) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McAfee Scanner (McODS) - McAfee, Inc. - C:\Program Files\McAfee\VirusScan\mcods.exe
O23 - Service: McAfee Proxy Service (McProxy) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: McShield - McAfee, Inc. - C:\Program Files\Common Files\McAfee\SystemCore\\mcshield.exe
O23 - Service: McAfee Firewall Core Service (mfefire) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\SystemCore\\mfefire.exe
O23 - Service: McAfee Validation Trust Protection Service (mfevtp) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\SystemCore\mfevtps.exe
O23 - Service: @comres.dll,-2797 (MSDTC) - Unknown owner - C:\Windows\System32\msdtc.exe (file missing)
O23 - Service: McAfee Anti-Spam Service (MSK80Service) - McAfee, Inc. - C:\Program Files\Common Files\McAfee\McSvcHost\McSvHost.exe
O23 - Service: @%SystemRoot%\System32\netlogon.dll,-102 (Netlogon) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: @%systemroot%\system32\psbase.dll,-300 (ProtectedStorage) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: Protexis Licensing V2 (PSI_SVC_2) - Protexis Inc. - c:\Program Files (x86)\Common Files\Protexis\License Service\PsiService_2.exe
O23 - Service: @%systemroot%\system32\Locator.exe,-2 (RpcLocator) - Unknown owner - C:\Windows\system32\locator.exe (file missing)
O23 - Service: @%SystemRoot%\system32\samsrv.dll,-1 (SamSs) - Unknown owner - C:\Windows\system32\lsass.exe (file missing)
O23 - Service: VIPRE Antivirus (SBAMSvc) - GFI Software - C:\Program Files (x86)\GFI Software\VIPRE\SBAMSvc.exe
O23 - Service: SB Recovery Service (SBPIMSvc) - GFI Software - C:\Program Files (x86)\GFI Software\VIPRE\SBPIMSvc.exe
O23 - Service: @%SystemRoot%\system32\SLsvc.exe,-101 (slsvc) - Unknown owner - C:\Windows\system32\SLsvc.exe (file missing)
O23 - Service: @%SystemRoot%\system32\snmptrap.exe,-3 (SNMPTRAP) - Unknown owner - C:\Windows\System32\snmptrap.exe (file missing)
O23 - Service: Sound Blaster X-Fi MB Licensing Service - Creative Labs - C:\Program Files (x86)\Common Files\Creative Labs Shared\Service\XMBLicensing.exe
O23 - Service: @%systemroot%\system32\spoolsv.exe,-1 (Spooler) - Unknown owner - C:\Windows\System32\spoolsv.exe (file missing)
O23 - Service: SupportSoft Sprocket Service (DellSupportCenter) (sprtsvc_DellSupportCenter) - SupportSoft, Inc. - C:\Program Files (x86)\Dell Support Center\bin\sprtsvc.exe
O23 - Service: stllssvr - MicroVision Development, Inc. - C:\Program Files (x86)\Common Files\SureThing Shared\stllssvr.exe
O23 - Service: Adobe SwitchBoard (SwitchBoard) - Adobe Systems Incorporated - C:\Program Files (x86)\Common Files\Adobe\SwitchBoard\SwitchBoard.exe
O23 - Service: @%SystemRoot%\system32\ui0detect.exe,-101 (UI0Detect) - Unknown owner - C:\Windows\system32\UI0Detect.exe (file missing)
O23 - Service: @%SystemRoot%\system32\vds.exe,-100 (vds) - Unknown owner - C:\Windows\System32\vds.exe (file missing)
O23 - Service: @%systemroot%\system32\vssvc.exe,-102 (VSS) - Unknown owner - C:\Windows\system32\vssvc.exe (file missing)
O23 - Service: @%Systemroot%\system32\wbem\wmiapsrv.exe,-110 (wmiApSrv) - Unknown owner - C:\Windows\system32\wbem\WmiApSrv.exe (file missing)
O23 - Service: @%ProgramFiles%\Windows Media Player\wmpnetwk.exe,-101 (WMPNetworkSvc) - Unknown owner - C:\Program Files (x86)\Windows Media Player\wmpnetwk.exe (file missing)
--
End of file - 17797 bytes
Ok, before we continue, are you missing any desktop icons or start menu programs? This is very common with todays new rogue programs. If you are missing icons and programs then please download and run unhide.exe.
Then do the following.
1.
Please download and run TDSSkiller
When the program opens, click on the start scan button.
TDSSKiller will now scan your computer for the TDSS infection. When the scan has finished it will display a result screen stating whether or not the infection was found on your computer. If it was found it will display a screen similar to the one below.
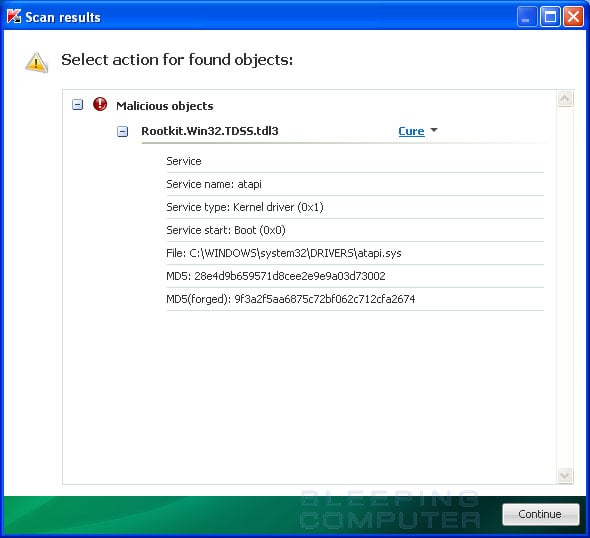
To remove the infection simply click on the Continue button and TDSSKiller will attempt to clean the infection.
When it has finished cleaning the infection you will see a report stating whether or not it was successful as shown below.
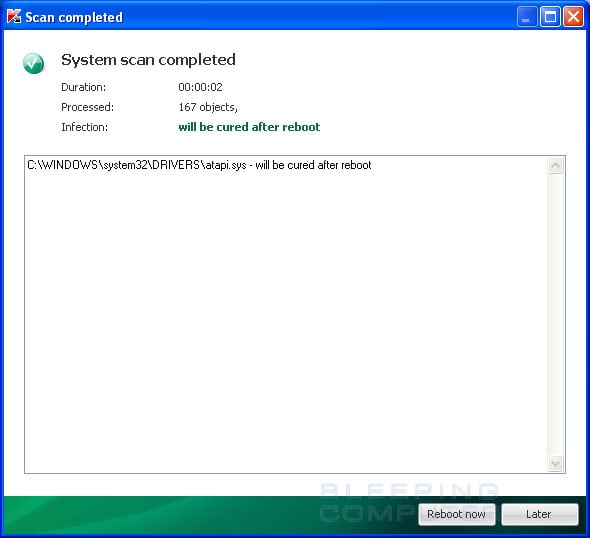
If the log says will be cured after reboot, please reboot the system by pressing the reboot now button.
After running there will be a log that will be located at the root of your c:\ drive labeled tdsskiller with a series of numbers after it. Please open the log and copy and paste it back here.
2.
Please make sure you follow the directions carefully, your mcafee program must be disabled before running combofix. Details on how to disable mcafee is included.
Download and Run ComboFix
If you already have Combofix, please delete this copy and download it again as it's being updated regularly.
In your next reply please post:
3.
I need you to post a log that combofix creates but doesn't automatically show you. Please navigate to C:\Qoobox and in that folder will be a file named add-remove programs.txt. PLease open that file and copy and paste the contents back here.
Then do the following.
1.
Please download and run TDSSkiller
When the program opens, click on the start scan button.
TDSSKiller will now scan your computer for the TDSS infection. When the scan has finished it will display a result screen stating whether or not the infection was found on your computer. If it was found it will display a screen similar to the one below.

To remove the infection simply click on the Continue button and TDSSKiller will attempt to clean the infection.
When it has finished cleaning the infection you will see a report stating whether or not it was successful as shown below.

If the log says will be cured after reboot, please reboot the system by pressing the reboot now button.
After running there will be a log that will be located at the root of your c:\ drive labeled tdsskiller with a series of numbers after it. Please open the log and copy and paste it back here.
2.
Please make sure you follow the directions carefully, your mcafee program must be disabled before running combofix. Details on how to disable mcafee is included.
Download and Run ComboFix
If you already have Combofix, please delete this copy and download it again as it's being updated regularly.
- Download this file here :
Combofix
- When the page loads click on the blue combofix download link next to the BleepingComputer Mirror.
- Save the file to your windows desktop. The combofix icon will look like this when it has downloaded to your desktop.

- We are almost ready to start ComboFix, but before we do so, we need to take some preventative measures so that there are no conflicts with other programs when running ComboFix. At this point you should do the following:
- Close all open Windows including this one.
- Close or disable all running Antivirus, Antispyware, and Firewall programs as they may interfere with the proper running of ComboFix. Instructions on disabling these type of programs can be found here.
Once these two steps have been completed, double-click on the ComboFix icon found on your desktop. Please note, that once you start ComboFix you should not click anywhere on the ComboFix window as it can cause the program to stall. In fact, when ComboFix is running, do not touch your computer at all. The scan could take a while, so please be patient.
- Please click on I agree on the disclaimer window.
- ComboFix will now install itself on to your computer. When it is done, a blue screen will appear as shown below.
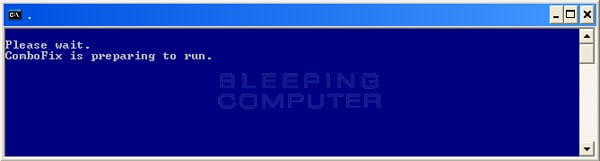
- ComboFix is now preparing to run. When it has finished ComboFix will automatically attempt to create a System Restore point so that if any problems occur while using the program you can restore back to your previous configuration. When ComboFix has finished creating the restore point, it will then backup your Windows Registry as shown in the image below.
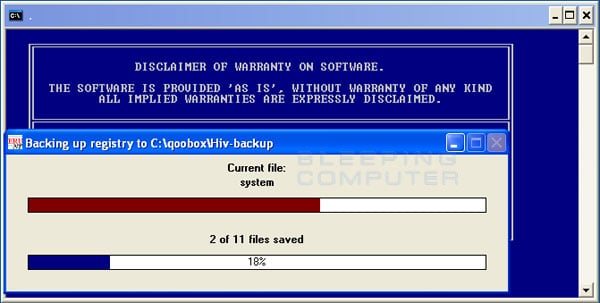
- Once the Windows Registry has finished being backed up, ComboFix will attempt to detect if you have the Windows Recovery Console installed. If you already have it installed, you can skip to this section and continue reading. Otherwise you will see the following message as shown below:
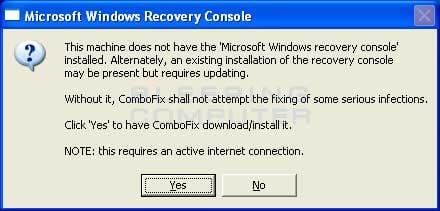
- At the above message box, please click on the Yes button in order for ComboFix to continue. Please follow the steps and instructions given by ComboFix in order to finish the installation of the Recovery Console.
- Please click on yes in the next window to continue scanning for malware.
- ComboFix will now disconnect your computer from the Internet, so do not be surprised or concerned if you receive any warnings stating that you are no longer on the Internet. When ComboFix has finished it will automatically restore your Internet connection.
- ComboFix will now start scanning your computer for known infections. This procedure can take some time, so please be patient.
- While the program is scanning your computer, it will change your clock format, so do not be concerned when you see this happen. When ComboFix is finished it will restore your clock settings to their previous settings. You will also see the text in the ComboFix window being updated as it goes through the various stages of its scan. An example of this can be seen below.
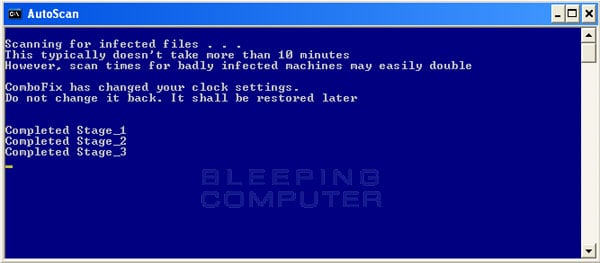
- When ComboFix has finished running, you will see a screen stating that it is preparing the log report.
- This can take a while, so please be patient. If you see your Windows desktop disappear, do not worry. This is normal and ComboFix will restore your desktop before it is finished. Eventually you will see a new screen that states the program is almost finished and telling you the programs log file, or report, will be located at C:\ComboFix.txt.
- When ComboFix has finished, it will automatically close the program and change your clock back to its original format. It will then display the log file automatically for you.
- Now you just click on the edit menu and click on select all, then click on the edit menu again and click on copy. Then come to the forum in your reply and right click on your mouse and click on paste.
In your next reply please post:
- The ComboFix log
- A fresh HiJackThis log
- An update on how your computer is running
3.
I need you to post a log that combofix creates but doesn't automatically show you. Please navigate to C:\Qoobox and in that folder will be a file named add-remove programs.txt. PLease open that file and copy and paste the contents back here.
Before I do something wrong, after running "unhide.exe" I got program icons back (although the placements are incorrect) on my #1 monitor but no program icons restored on my #2 monitor (I use extended desktop). Also, no folders or saved photos icons were restored.
I also ran "TDSSkiller" but did not get a "Cure" option on the drop-down menu, only "Skip", "Copy to quarantine" and "Delete". I did get a "Report" but it will not copy so I can past it.
I have done no rebooting.
Am I on the right track?
I also ran "TDSSkiller" but did not get a "Cure" option on the drop-down menu, only "Skip", "Copy to quarantine" and "Delete". I did get a "Report" but it will not copy so I can past it.
I have done no rebooting.
Am I on the right track?
[InfectedFile]
Type: Raw image
Src: c:\program files (x86)\common files\akamai/netsession_win_6c825ce.dll
md5: 1125c7d9fb8898015829c387c1bc87c7
[InfectedObject]
Type: Service
Name: Akamai
Type: n/a (0x110)
Start: Auto (0x2)
ImagePath: %SystemRoot%\System32\svchost.exe -k Akamai
Suspicious states: Hidden file;
Type: Raw image
Src: c:\program files (x86)\common files\akamai/netsession_win_6c825ce.dll
md5: 1125c7d9fb8898015829c387c1bc87c7
[InfectedObject]
Type: Service
Name: Akamai
Type: n/a (0x110)
Start: Auto (0x2)
ImagePath: %SystemRoot%\System32\svchost.exe -k Akamai
Suspicious states: Hidden file;
[InfectedFile]
Type: Raw image
Src: c:\program files (x86)\common files\akamai/netsession_win_6c825ce.dll
md5: 1125c7d9fb8898015829c387c1bc87c7
[InfectedObject]
Type: Service
Name: Akamai
Type: n/a (0x110)
Start: Auto (0x2)
ImagePath: %SystemRoot%\System32\svchost.exe -k Akamai
Suspicious states: Hidden file;
what program is telling you these files are infected? tdsskiller? if so, skip for now and run combofix.
