2011/08/10 09:43:39.0093 0260 TDSS rootkit removing tool 2.5.14.0 Aug 5 2011 16:09:29
2011/08/10 09:43:39.0484 0260 ================================================================================
2011/08/10 09:43:39.0484 0260 SystemInfo:
2011/08/10 09:43:39.0484 0260
2011/08/10 09:43:39.0484 0260 OS Version: 5.1.2600 ServicePack: 3.0
2011/08/10 09:43:39.0484 0260 Product type: Workstation
2011/08/10 09:43:39.0484 0260 ComputerName: BRYCE-BTQQZPZU3
2011/08/10 09:43:39.0484 0260 UserName: Bryce Riebel
2011/08/10 09:43:39.0484 0260 Windows directory: C:\WINDOWS
2011/08/10 09:43:39.0484 0260 System windows directory: C:\WINDOWS
2011/08/10 09:43:39.0484 0260 Processor architecture: Intel x86
2011/08/10 09:43:39.0484 0260 Number of processors: 1
2011/08/10 09:43:39.0484 0260 Page size: 0x1000
2011/08/10 09:43:39.0484 0260 Boot type: Normal boot
2011/08/10 09:43:39.0484 0260 ================================================================================
2011/08/10 09:43:40.0562 0260 Initialize success
2011/08/10 09:43:44.0390 0172 ================================================================================
2011/08/10 09:43:44.0390 0172 Scan started
2011/08/10 09:43:44.0390 0172 Mode: Manual;
2011/08/10 09:43:44.0390 0172 ================================================================================
2011/08/10 09:43:45.0796 0172 ACPI (8fd99680a539792a30e97944fdaecf17) C:\WINDOWS\system32\DRIVERS\ACPI.sys
2011/08/10 09:43:45.0843 0172 ACPIEC (9859c0f6936e723e4892d7141b1327d5) C:\WINDOWS\system32\drivers\ACPIEC.sys
2011/08/10 09:43:45.0921 0172 aec (8bed39e3c35d6a489438b8141717a557) C:\WINDOWS\system32\drivers\aec.sys
2011/08/10 09:43:45.0984 0172 AFD (7e775010ef291da96ad17ca4b17137d7) C:\WINDOWS\System32\drivers\afd.sys
2011/08/10 09:43:46.0093 0172 agp440 (08fd04aa961bdc77fb983f328334e3d7) C:\WINDOWS\system32\DRIVERS\agp440.sys
2011/08/10 09:43:46.0390 0172 AsyncMac (b153affac761e7f5fcfa822b9c4e97bc) C:\WINDOWS\system32\DRIVERS\asyncmac.sys
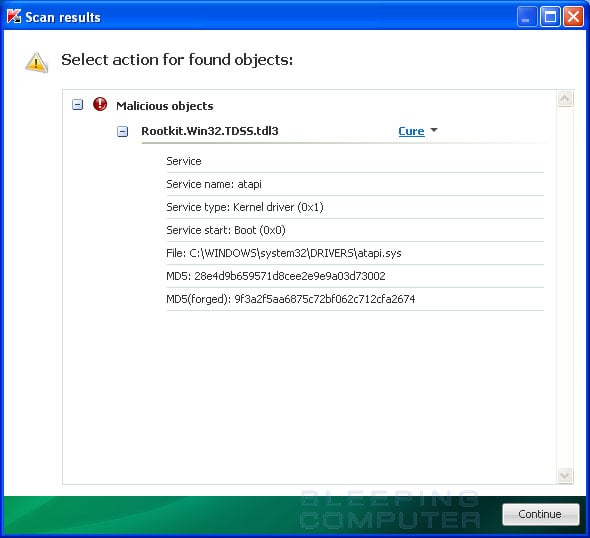
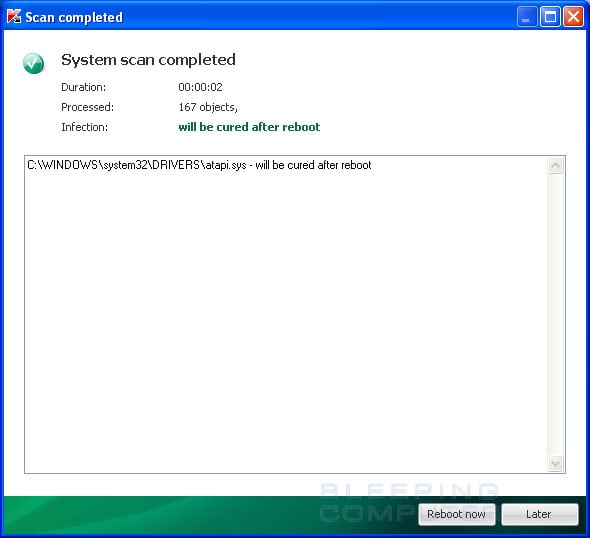
2011/08/10 09:43:46.0421 0172 atapi (9f3a2f5aa6875c72bf062c712cfa2674) C:\WINDOWS\system32\DRIVERS\atapi.sys
2011/08/10 09:43:46.0468 0172 Atmarpc (9916c1225104ba14794209cfa8012159) C:\WINDOWS\system32\DRIVERS\atmarpc.sys
2011/08/10 09:43:46.0531 0172 audstub (d9f724aa26c010a217c97606b160ed68) C:\WINDOWS\system32\DRIVERS\audstub.sys
2011/08/10 09:43:46.0593 0172 BANTExt (5d7be7b19e827125e016325334e58ff1) C:\WINDOWS\System32\Drivers\BANTExt.sys
2011/08/10 09:43:46.0656 0172 Beep (da1f27d85e0d1525f6621372e7b685e9) C:\WINDOWS\system32\drivers\Beep.sys
2011/08/10 09:43:46.0718 0172 cbidf2k (90a673fc8e12a79afbed2576f6a7aaf9) C:\WINDOWS\system32\drivers\cbidf2k.sys
2011/08/10 09:43:46.0781 0172 Cdaudio (c1b486a7658353d33a10cc15211a873b) C:\WINDOWS\system32\drivers\Cdaudio.sys
2011/08/10 09:43:46.0828 0172 Cdfs (c885b02847f5d2fd45a24e219ed93b32) C:\WINDOWS\system32\drivers\Cdfs.sys
2011/08/10 09:43:46.0859 0172 Cdrom (1f4260cc5b42272d71f79e570a27a4fe) C:\WINDOWS\system32\DRIVERS\cdrom.sys
2011/08/10 09:43:47.0046 0172 ctsfm2k (8db84de3aab34a8b4c2f644eff41cd76) C:\WINDOWS\system32\DRIVERS\ctsfm2k.sys
2011/08/10 09:43:47.0156 0172 Disk (044452051f3e02e7963599fc8f4f3e25) C:\WINDOWS\system32\DRIVERS\disk.sys
2011/08/10 09:43:47.0218 0172 dmboot (d992fe1274bde0f84ad826acae022a41) C:\WINDOWS\system32\drivers\dmboot.sys
2011/08/10 09:43:47.0359 0172 dmio (7c824cf7bbde77d95c08005717a95f6f) C:\WINDOWS\system32\drivers\dmio.sys
2011/08/10 09:43:47.0468 0172 dmload (e9317282a63ca4d188c0df5e09c6ac5f) C:\WINDOWS\system32\drivers\dmload.sys
2011/08/10 09:43:47.0531 0172 DMusic (8a208dfcf89792a484e76c40e5f50b45) C:\WINDOWS\system32\drivers\DMusic.sys
2011/08/10 09:43:47.0625 0172 drmkaud (8f5fcff8e8848afac920905fbd9d33c8) C:\WINDOWS\system32\drivers\drmkaud.sys
2011/08/10 09:43:47.0687 0172 E100B (d57a8fc800b501ac05b10d00f66d127a) C:\WINDOWS\system32\DRIVERS\e100b325.sys
2011/08/10 09:43:47.0812 0172 FA312 (aa855fb8a866281aacb393c1feab91ae) C:\WINDOWS\system32\DRIVERS\FA312nd5.sys
2011/08/10 09:43:47.0875 0172 Fastfat (38d332a6d56af32635675f132548343e) C:\WINDOWS\system32\drivers\Fastfat.sys
2011/08/10 09:43:48.0000 0172 Fdc (92cdd60b6730b9f50f6a1a0c1f8cdc81) C:\WINDOWS\system32\DRIVERS\fdc.sys
2011/08/10 09:43:48.0109 0172 Fips (d45926117eb9fa946a6af572fbe1caa3) C:\WINDOWS\system32\drivers\Fips.sys
2011/08/10 09:43:48.0218 0172 Flpydisk (9d27e7b80bfcdf1cdd9b555862d5e7f0) C:\WINDOWS\system32\drivers\Flpydisk.sys
2011/08/10 09:43:48.0328 0172 FltMgr (b2cf4b0786f8212cb92ed2b50c6db6b0) C:\WINDOWS\system32\drivers\fltmgr.sys
2011/08/10 09:43:48.0437 0172 Fs_Rec (3e1e2bd4f39b0e2b7dc4f4d2bcc2779a) C:\WINDOWS\system32\drivers\Fs_Rec.sys
2011/08/10 09:43:48.0468 0172 Ftdisk (6ac26732762483366c3969c9e4d2259d) C:\WINDOWS\system32\DRIVERS\ftdisk.sys
2011/08/10 09:43:48.0546 0172 GEARAspiWDM (8182ff89c65e4d38b2de4bb0fb18564e) C:\WINDOWS\system32\DRIVERS\GEARAspiWDM.sys
2011/08/10 09:43:48.0593 0172 Gpc (0a02c63c8b144bd8c86b103dee7c86a2) C:\WINDOWS\system32\DRIVERS\msgpc.sys
2011/08/10 09:43:48.0687 0172 HPZid412 (d03d10f7ded688fecf50f8fbf1ea9b8a) C:\WINDOWS\system32\DRIVERS\HPZid412.sys
2011/08/10 09:43:48.0734 0172 HPZipr12 (08cb72e95dd75b61f2966b311d0e4366) C:\WINDOWS\system32\DRIVERS\HPZipr12.sys
2011/08/10 09:43:48.0781 0172 HPZius12 (abcb05ccdbf03000354b9553820e39f8) C:\WINDOWS\system32\DRIVERS\HPZius12.sys
2011/08/10 09:43:48.0843 0172 HTTP (f80a415ef82cd06ffaf0d971528ead38) C:\WINDOWS\system32\Drivers\HTTP.sys
2011/08/10 09:43:49.0000 0172 i8042prt (4a0b06aa8943c1e332520f7440c0aa30) C:\WINDOWS\system32\DRIVERS\i8042prt.sys
2011/08/10 09:43:49.0046 0172 Imapi (083a052659f5310dd8b6a6cb05edcf8e) C:\WINDOWS\system32\DRIVERS\imapi.sys
2011/08/10 09:43:49.0140 0172 intelppm (8c953733d8f36eb2133f5bb58808b66b) C:\WINDOWS\system32\DRIVERS\intelppm.sys
2011/08/10 09:43:49.0187 0172 ip6fw (3bb22519a194418d5fec05d800a19ad0) C:\WINDOWS\system32\drivers\ip6fw.sys
2011/08/10 09:43:49.0296 0172 IpFilterDriver (731f22ba402ee4b62748adaf6363c182) C:\WINDOWS\system32\DRIVERS\ipfltdrv.sys
2011/08/10 09:43:49.0343 0172 IpInIp (b87ab476dcf76e72010632b5550955f5) C:\WINDOWS\system32\DRIVERS\ipinip.sys
2011/08/10 09:43:49.0390 0172 IpNat (cc748ea12c6effde940ee98098bf96bb) C:\WINDOWS\system32\DRIVERS\ipnat.sys
2011/08/10 09:43:49.0437 0172 IPSec (23c74d75e36e7158768dd63d92789a91) C:\WINDOWS\system32\DRIVERS\ipsec.sys
2011/08/10 09:43:49.0484 0172 IRENUM (c93c9ff7b04d772627a3646d89f7bf89) C:\WINDOWS\system32\DRIVERS\irenum.sys
2011/08/10 09:43:49.0546 0172 isapnp (05a299ec56e52649b1cf2fc52d20f2d7) C:\WINDOWS\system32\DRIVERS\isapnp.sys
2011/08/10 09:43:49.0578 0172 Kbdclass (463c1ec80cd17420a542b7f36a36f128) C:\WINDOWS\system32\DRIVERS\kbdclass.sys
2011/08/10 09:43:49.0640 0172 kmixer (692bcf44383d056aed41b045a323d378) C:\WINDOWS\system32\drivers\kmixer.sys
2011/08/10 09:43:49.0703 0172 KSecDD (b467646c54cc746128904e1654c750c1) C:\WINDOWS\system32\drivers\KSecDD.sys
2011/08/10 09:43:49.0843 0172 MBAMSwissArmy (b18225739ed9caa83ba2df966e9f43e8) C:\WINDOWS\system32\drivers\mbamswissarmy.sys
2011/08/10 09:43:49.0906 0172 mnmdd (4ae068242760a1fb6e1a44bf4e16afa6) C:\WINDOWS\system32\drivers\mnmdd.sys
2011/08/10 09:43:49.0953 0172 Modem (dfcbad3cec1c5f964962ae10e0bcc8e1) C:\WINDOWS\system32\drivers\Modem.sys
2011/08/10 09:43:49.0984 0172 Mouclass (35c9e97194c8cfb8430125f8dbc34d04) C:\WINDOWS\system32\DRIVERS\mouclass.sys
2011/08/10 09:43:50.0046 0172 MountMgr (a80b9a0bad1b73637dbcbba7df72d3fd) C:\WINDOWS\system32\drivers\MountMgr.sys
2011/08/10 09:43:50.0109 0172 MRxDAV (11d42bb6206f33fbb3ba0288d3ef81bd) C:\WINDOWS\system32\DRIVERS\mrxdav.sys
2011/08/10 09:43:50.0171 0172 MRxSmb (f3aefb11abc521122b67095044169e98) C:\WINDOWS\system32\DRIVERS\mrxsmb.sys
2011/08/10 09:43:50.0343 0172 Msfs (c941ea2454ba8350021d774daf0f1027) C:\WINDOWS\system32\drivers\Msfs.sys
2011/08/10 09:43:50.0406 0172 MSKSSRV (d1575e71568f4d9e14ca56b7b0453bf1) C:\WINDOWS\system32\drivers\MSKSSRV.sys
2011/08/10 09:43:50.0437 0172 MSPCLOCK (325bb26842fc7ccc1fcce2c457317f3e) C:\WINDOWS\system32\drivers\MSPCLOCK.sys
2011/08/10 09:43:50.0484 0172 MSPQM (bad59648ba099da4a17680b39730cb3d) C:\WINDOWS\system32\drivers\MSPQM.sys
2011/08/10 09:43:50.0531 0172 mssmbios (af5f4f3f14a8ea2c26de30f7a1e17136) C:\WINDOWS\system32\DRIVERS\mssmbios.sys
2011/08/10 09:43:50.0593 0172 Mup (2f625d11385b1a94360bfc70aaefdee1) C:\WINDOWS\system32\drivers\Mup.sys
2011/08/10 09:43:50.0718 0172 NDIS (1df7f42665c94b825322fae71721130d) C:\WINDOWS\system32\drivers\NDIS.sys
2011/08/10 09:43:50.0828 0172 NdisTapi (1ab3d00c991ab086e69db84b6c0ed78f) C:\WINDOWS\system32\DRIVERS\ndistapi.sys
2011/08/10 09:43:50.0859 0172 Ndisuio (f927a4434c5028758a842943ef1a3849) C:\WINDOWS\system32\DRIVERS\ndisuio.sys
2011/08/10 09:43:50.0875 0172 NdisWan (edc1531a49c80614b2cfda43ca8659ab) C:\WINDOWS\system32\DRIVERS\ndiswan.sys
2011/08/10 09:43:50.0937 0172 NDProxy (9282bd12dfb069d3889eb3fcc1000a9b) C:\WINDOWS\system32\drivers\NDProxy.sys
2011/08/10 09:43:51.0000 0172 NetBIOS (5d81cf9a2f1a3a756b66cf684911cdf0) C:\WINDOWS\system32\DRIVERS\netbios.sys
2011/08/10 09:43:51.0046 0172 NetBT (74b2b2f5bea5e9a3dc021d685551bd3d) C:\WINDOWS\system32\DRIVERS\netbt.sys
2011/08/10 09:43:51.0109 0172 Npfs (3182d64ae053d6fb034f44b6def8034a) C:\WINDOWS\system32\drivers\Npfs.sys
2011/08/10 09:43:51.0156 0172 Ntfs (78a08dd6a8d65e697c18e1db01c5cdca) C:\WINDOWS\system32\drivers\Ntfs.sys
2011/08/10 09:43:51.0296 0172 Null (73c1e1f395918bc2c6dd67af7591a3ad) C:\WINDOWS\system32\drivers\Null.sys
2011/08/10 09:43:51.0531 0172 nv (9f4384aa43548ddd438f7b7825d11699) C:\WINDOWS\system32\DRIVERS\nv4_mini.sys
2011/08/10 09:43:51.0703 0172 NwlnkFlt (b305f3fad35083837ef46a0bbce2fc57) C:\WINDOWS\system32\DRIVERS\nwlnkflt.sys
2011/08/10 09:43:51.0750 0172 NwlnkFwd (c99b3415198d1aab7227f2c88fd664b9) C:\WINDOWS\system32\DRIVERS\nwlnkfwd.sys
2011/08/10 09:43:51.0812 0172 ossrv (103a9b117a7d9903111955cdafe65ac6) C:\WINDOWS\system32\DRIVERS\ctoss2k.sys
2011/08/10 09:43:51.0875 0172 P17 (df886ffed69aead0cf608b89b18c3f6f) C:\WINDOWS\system32\drivers\P17.sys
2011/08/10 09:43:52.0015 0172 Parport (5575faf8f97ce5e713d108c2a58d7c7c) C:\WINDOWS\system32\DRIVERS\parport.sys
2011/08/10 09:43:52.0046 0172 PartMgr (beb3ba25197665d82ec7065b724171c6) C:\WINDOWS\system32\drivers\PartMgr.sys
2011/08/10 09:43:52.0109 0172 ParVdm (70e98b3fd8e963a6a46a2e6247e0bea1) C:\WINDOWS\system32\drivers\ParVdm.sys
2011/08/10 09:43:52.0171 0172 PCI (a219903ccf74233761d92bef471a07b1) C:\WINDOWS\system32\DRIVERS\pci.sys
2011/08/10 09:43:52.0234 0172 PCIIde (ccf5f451bb1a5a2a522a76e670000ff0) C:\WINDOWS\system32\DRIVERS\pciide.sys
2011/08/10 09:43:52.0281 0172 Pcmcia (9e89ef60e9ee05e3f2eef2da7397f1c1) C:\WINDOWS\system32\drivers\Pcmcia.sys
2011/08/10 09:43:52.0515 0172 PptpMiniport (efeec01b1d3cf84f16ddd24d9d9d8f99) C:\WINDOWS\system32\DRIVERS\raspptp.sys
2011/08/10 09:43:52.0546 0172 Processor (a32bebaf723557681bfc6bd93e98bd26) C:\WINDOWS\system32\DRIVERS\processr.sys
2011/08/10 09:43:52.0578 0172 PSched (09298ec810b07e5d582cb3a3f9255424) C:\WINDOWS\system32\DRIVERS\psched.sys
2011/08/10 09:43:52.0625 0172 Ptilink (80d317bd1c3dbc5d4fe7b1678c60cadd) C:\WINDOWS\system32\DRIVERS\ptilink.sys
2011/08/10 09:43:52.0781 0172 RasAcd (fe0d99d6f31e4fad8159f690d68ded9c) C:\WINDOWS\system32\DRIVERS\rasacd.sys
2011/08/10 09:43:52.0843 0172 Rasl2tp (11b4a627bc9614b885c4969bfa5ff8a6) C:\WINDOWS\system32\DRIVERS\rasl2tp.sys
2011/08/10 09:43:52.0890 0172 RasPppoe (5bc962f2654137c9909c3d4603587dee) C:\WINDOWS\system32\DRIVERS\raspppoe.sys
2011/08/10 09:43:52.0953 0172 Raspti (fdbb1d60066fcfbb7452fd8f9829b242) C:\WINDOWS\system32\DRIVERS\raspti.sys
2011/08/10 09:43:53.0000 0172 Rdbss (7ad224ad1a1437fe28d89cf22b17780a) C:\WINDOWS\system32\DRIVERS\rdbss.sys
2011/08/10 09:43:53.0109 0172 RDPCDD (4912d5b403614ce99c28420f75353332) C:\WINDOWS\system32\DRIVERS\RDPCDD.sys
2011/08/10 09:43:53.0171 0172 rdpdr (15cabd0f7c00c47c70124907916af3f1) C:\WINDOWS\system32\DRIVERS\rdpdr.sys
2011/08/10 09:43:53.0281 0172 RDPWD (6728e45b66f93c08f11de2e316fc70dd) C:\WINDOWS\system32\drivers\RDPWD.sys
2011/08/10 09:43:53.0406 0172 redbook (f828dd7e1419b6653894a8f97a0094c5) C:\WINDOWS\system32\DRIVERS\redbook.sys
2011/08/10 09:43:53.0546 0172 Secdrv (90a3935d05b494a5a39d37e71f09a677) C:\WINDOWS\system32\DRIVERS\secdrv.sys
2011/08/10 09:43:53.0687 0172 serenum (0f29512ccd6bead730039fb4bd2c85ce) C:\WINDOWS\system32\DRIVERS\serenum.sys
2011/08/10 09:43:53.0781 0172 Serial (cca207a8896d4c6a0c9ce29a4ae411a7) C:\WINDOWS\system32\DRIVERS\serial.sys
2011/08/10 09:43:53.0937 0172 Sfloppy (8e6b8c671615d126fdc553d1e2de5562) C:\WINDOWS\system32\drivers\Sfloppy.sys
2011/08/10 09:43:54.0109 0172 splitter (ab8b92451ecb048a4d1de7c3ffcb4a9f) C:\WINDOWS\system32\drivers\splitter.sys
2011/08/10 09:43:54.0218 0172 sr (76bb022c2fb6902fd5bdd4f78fc13a5d) C:\WINDOWS\system32\DRIVERS\sr.sys
2011/08/10 09:43:54.0343 0172 Srv (0f6aefad3641a657e18081f52d0c15af) C:\WINDOWS\system32\DRIVERS\srv.sys
2011/08/10 09:43:54.0468 0172 swenum (3941d127aef12e93addf6fe6ee027e0f) C:\WINDOWS\system32\DRIVERS\swenum.sys
2011/08/10 09:43:54.0546 0172 swmidi (8ce882bcc6cf8a62f2b2323d95cb3d01) C:\WINDOWS\system32\drivers\swmidi.sys
2011/08/10 09:43:54.0750 0172 sysaudio (8b83f3ed0f1688b4958f77cd6d2bf290) C:\WINDOWS\system32\drivers\sysaudio.sys
2011/08/10 09:43:54.0875 0172 Tcpip (9aefa14bd6b182d61e3119fa5f436d3d) C:\WINDOWS\system32\DRIVERS\tcpip.sys
2011/08/10 09:43:54.0984 0172 TDPIPE (6471a66807f5e104e4885f5b67349397) C:\WINDOWS\system32\drivers\TDPIPE.sys
2011/08/10 09:43:55.0078 0172 TDTCP (c56b6d0402371cf3700eb322ef3aaf61) C:\WINDOWS\system32\drivers\TDTCP.sys
2011/08/10 09:43:55.0125 0172 TermDD (88155247177638048422893737429d9e) C:\WINDOWS\system32\DRIVERS\termdd.sys
2011/08/10 09:43:55.0203 0172 Udfs (5787b80c2e3c5e2f56c2a233d91fa2c9) C:\WINDOWS\system32\drivers\Udfs.sys
2011/08/10 09:43:55.0296 0172 Update (402ddc88356b1bac0ee3dd1580c76a31) C:\WINDOWS\system32\DRIVERS\update.sys
2011/08/10 09:43:55.0421 0172 USBAAPL (83cafcb53201bbac04d822f32438e244) C:\WINDOWS\system32\Drivers\usbaapl.sys
2011/08/10 09:43:55.0515 0172 usbccgp (173f317ce0db8e21322e71b7e60a27e8) C:\WINDOWS\system32\DRIVERS\usbccgp.sys
2011/08/10 09:43:55.0625 0172 usbehci (65dcf09d0e37d4c6b11b5b0b76d470a7) C:\WINDOWS\system32\DRIVERS\usbehci.sys
2011/08/10 09:43:55.0718 0172 usbhub (1ab3cdde553b6e064d2e754efe20285c) C:\WINDOWS\system32\DRIVERS\usbhub.sys
2011/08/10 09:43:55.0781 0172 usbprint (a717c8721046828520c9edf31288fc00) C:\WINDOWS\system32\DRIVERS\usbprint.sys
2011/08/10 09:43:55.0875 0172 usbscan (a0b8cf9deb1184fbdd20784a58fa75d4) C:\WINDOWS\system32\DRIVERS\usbscan.sys
2011/08/10 09:43:55.0984 0172 USBSTOR (a32426d9b14a089eaa1d922e0c5801a9) C:\WINDOWS\system32\DRIVERS\USBSTOR.SYS
2011/08/10 09:43:56.0093 0172 usbuhci (26496f9dee2d787fc3e61ad54821ffe6) C:\WINDOWS\system32\DRIVERS\usbuhci.sys
2011/08/10 09:43:56.0203 0172 VgaSave (0d3a8fafceacd8b7625cd549757a7df1) C:\WINDOWS\System32\drivers\vga.sys
2011/08/10 09:43:56.0328 0172 VolSnap (4c8fcb5cc53aab716d810740fe59d025) C:\WINDOWS\system32\drivers\VolSnap.sys
2011/08/10 09:43:56.0453 0172 Wanarp (e20b95baedb550f32dd489265c1da1f6) C:\WINDOWS\system32\DRIVERS\wanarp.sys
2011/08/10 09:43:56.0578 0172 wdmaud (6768acf64b18196494413695f0c3a00f) C:\WINDOWS\system32\drivers\wdmaud.sys
2011/08/10 09:43:56.0718 0172 MBR (0x1B8) (8f558eb6672622401da993e1e865c861) \Device\Harddisk0\DR0
2011/08/10 09:43:56.0843 0172 Boot (0x1200) (8e11c99fd4651a375d7a1b531d777f23) \Device\Harddisk0\DR0\Partition0
2011/08/10 09:43:56.0859 0172 ================================================================================
2011/08/10 09:43:56.0859 0172 Scan finished
2011/08/10 09:43:56.0859 0172 ================================================================================
2011/08/10 09:43:56.0906 1240 Detected object count: 0
2011/08/10 09:43:56.0906 1240 Actual detected object count: 0
ComboFix 11-08-10.01 - Bryce Riebel 08/10/2011 9:52.1.1 - x86
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.2047.1573 [GMT -4:00]
Running from: c:\documents and settings\Bryce Riebel\Desktop\ComboFix.exe
* Created a new restore point
.
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
c:\program files\messenger\msmsgsin.exe
.
.
((((((((((((((((((((((((( Files Created from 2011-07-10 to 2011-08-10 )))))))))))))))))))))))))))))))
.
.
2011-08-10 13:41 . 2011-08-10 13:41 -------- d-----w- c:\program files\Common Files\Java
2011-08-01 00:50 . 2011-08-01 00:50 -------- d-----w- c:\documents and settings\Bryce Riebel\Application Data\Razor
2011-07-30 19:27 . 2011-07-30 19:27 -------- d-----w- c:\program files\Amazon
2011-07-26 00:54 . 2011-07-26 00:54 388096 ----a-r- c:\documents and settings\Bryce Riebel\Application Data\Microsoft\Installer\{45A66726-69BC-466B-A7A4-12FCBA4883D7}\HiJackThis.exe
2011-07-26 00:54 . 2011-07-26 00:54 -------- d-----w- c:\program files\Trend Micro
2011-07-26 00:37 . 2011-07-26 00:37 -------- d-----w- c:\documents and settings\Bryce Riebel\Application Data\Malwarebytes
2011-07-26 00:37 . 2011-07-06 23:52 41272 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2011-07-26 00:37 . 2011-07-26 00:37 -------- d-----w- c:\documents and settings\All Users\Application Data\Malwarebytes
2011-07-26 00:37 . 2011-07-26 00:37 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2011-07-26 00:37 . 2011-07-06 23:52 22712 ----a-w- c:\windows\system32\drivers\mbam.sys
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2011-08-10 13:30 . 2011-06-13 01:11 404640 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"NvCplDaemon"="c:\windows\System32\NvCpl.dll" [2008-05-16 13529088]
"nwiz"="nwiz.exe" [2008-05-16 1630208]
"NvMediaCenter"="c:\windows\System32\NvMcTray.dll" [2008-05-16 86016]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 9.0\Reader\Reader_sl.exe" [2011-06-08 37296]
"Adobe ARM"="c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2011-03-30 937920]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2010-11-29 421888]
"SunJavaUpdateSched"="c:\program files\Common Files\Java\Java Update\jusched.exe" [2011-04-08 254696]
.
c:\documents and settings\All Users\Start Menu\Programs\Startup\
hp psc 2000 Series.lnk - c:\program files\Hewlett-Packard\Digital Imaging\bin\hpobnz08.exe [2003-4-9 323646]
hpoddt01.exe.lnk - c:\program files\Hewlett-Packard\Digital Imaging\bin\hpotdd01.exe [2003-4-9 28672]
Microsoft Office.lnk - c:\program files\Microsoft Office\Office10\OSA.EXE [2001-2-13 83360]
.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\MSIServer]
@="Service"
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\services]
"Bonjour Service"=2 (0x2)
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"AntiVirusOverride"=dword:00000001
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
"DisableNotifications"= 1 (0x1)
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\EA GAMES\\Ultima Online Gold\\client.exe"=
"c:\\Program Files\\Bonjour\\mDNSResponder.exe"=
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"24726:TCP"= 24726:TCP:FlipShareServer
"24727:TCP"= 24727:TCP:FlipShareServer
.
R2 FlipShareServer;FlipShare Server;c:\program files\Flip Video\FlipShareServer\FlipShareServer.exe [12/15/2010 2:22 PM 1085440]
R4 MBAMSwissArmy;MBAMSwissArmy;c:\windows\system32\drivers\mbamswissarmy.sys [7/25/2011 8:37 PM 41272]
S2 clr_optimization_v4.0.30319_32;Microsoft .NET Framework NGEN v4.0.30319_X86;c:\windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe [3/18/2010 1:16 PM 130384]
S3 WPFFontCache_v0400;Windows Presentation Foundation Font Cache 4.0.0.0;c:\windows\Microsoft.NET\Framework\v4.0.30319\WPF\WPFFontCache_v0400.exe [3/18/2010 1:16 PM 753504]
.
--- Other Services/Drivers In Memory ---
.
*NewlyCreated* - 08317434
*NewlyCreated* - JAVAQUICKSTARTERSERVICE
*NewlyCreated* - MBAMSWISSARMY
*Deregistered* - 08317434
.
Contents of the 'Scheduled Tasks' folder
.
2011-06-29 c:\windows\Tasks\AppleSoftwareUpdate.job
- c:\program files\Apple Software Update\SoftwareUpdate.exe [2009-10-22 21:57]
.
2010-04-18 c:\windows\Tasks\FRU Task 2003-04-10 00:56ewlett-Packard2003-04-10 00:56p psc 2100 series272A572217594EBCF1CEE215E352B92AD073FDE4267577247.job
- c:\program files\Hewlett-Packard\Digital Imaging\Bin\hpqfrucl.exe [2003-04-09 22:56]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.google.com/
uInternet Settings,ProxyOverride = *.local
uInternet Settings,ProxyServer = http=127.0.0.1:55030
TCP: DhcpNameServer = 209.18.47.61 209.18.47.62
.
- - - - ORPHANS REMOVED - - - -
.
Toolbar-Locked - (no file)
HKLM-Run-iTunesHelper - e:\my music\iTunes\iTunesHelper.exe
MSConfigStartUp-PhotoJoy - c:\program files\PhotoJoy\bin\PhotoJoy.exe
.
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer,
http://www.gmer.net
Rootkit scan 2011-08-10 09:56
Windows 5.1.2600 Service Pack 3 NTFS
.
scanning hidden processes ...
.
scanning hidden autostart entries ...
.
scanning hidden files ...
.
scan completed successfully
hidden files: 0
.
**************************************************************************
.
Completion time: 2011-08-10 09:58:21
ComboFix-quarantined-files.txt 2011-08-10 13:58
.
Pre-Run: 80,902,459,392 bytes free
Post-Run: 80,956,973,056 bytes free
.
WindowsXP-KB310994-SP2-Pro-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
UnsupportedDebug="do not select this" /debug
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /fastdetect /NoExecute=OptIn
.
- - End Of File - - 377B87DA3424795C7012EA74B4911B77
On a hunch I downloaded and tried to install the current version of Windows Update Agent. Ended up having to force install it but now have Windows Update working again.
Not sure if these steps removed the virus or not.