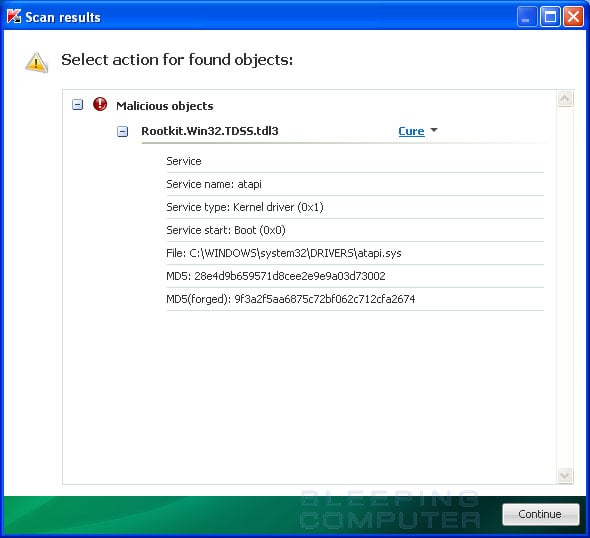
After running there will be a log that will be located at the root of your c:\ drive labeled tdsskiller with a series of numbers after it. Please open the log and copy and paste it back here.
I managed to get a zip of it by a friend attaching it to an email. The.exe wouldn't run, but after a couple of reboots it finally ran and found one threat. Here's the log.
2011/06/16 21:40:28.0312 5684 TDSS rootkit removing tool 2.5.5.0 Jun 16 2011 15:25:15
2011/06/16 21:40:29.0202 5684 ================================================================================
2011/06/16 21:40:29.0202 5684 SystemInfo:
2011/06/16 21:40:29.0202 5684
2011/06/16 21:40:29.0202 5684 OS Version: 6.0.6001 ServicePack: 1.0
2011/06/16 21:40:29.0202 5684 Product type: Workstation
2011/06/16 21:40:29.0202 5684 ComputerName: ANDREW-PC
2011/06/16 21:40:29.0202 5684 UserName: Andrew
2011/06/16 21:40:29.0202 5684 Windows directory: C:\Windows
2011/06/16 21:40:29.0202 5684 System windows directory: C:\Windows
2011/06/16 21:40:29.0202 5684 Processor architecture: Intel x86
2011/06/16 21:40:29.0202 5684 Number of processors: 2
2011/06/16 21:40:29.0202 5684 Page size: 0x1000
2011/06/16 21:40:29.0202 5684 Boot type: Normal boot
2011/06/16 21:40:29.0202 5684 ================================================================================
2011/06/16 21:40:32.0259 5684 Initialize success
2011/06/16 21:40:40.0044 6012 ================================================================================
2011/06/16 21:40:40.0044 6012 Scan started
2011/06/16 21:40:40.0044 6012 Mode: Manual;
2011/06/16 21:40:40.0044 6012 ================================================================================
2011/06/16 21:40:45.0987 6012 ACPI (fcb8c7210f0135e24c6580f7f649c73c) C:\Windows\system32\drivers\acpi.sys
2011/06/16 21:40:46.0580 6012 adp94xx (04f0fcac69c7c71a3ac4eb97fafc8303) C:\Windows\system32\drivers\adp94xx.sys
2011/06/16 21:40:47.0017 6012 adpahci (60505e0041f7751bdbb80f88bf45c2ce) C:\Windows\system32\drivers\adpahci.sys
2011/06/16 21:40:47.0407 6012 adpu160m (8a42779b02aec986eab64ecfc98f8bd7) C:\Windows\system32\drivers\adpu160m.sys
2011/06/16 21:40:48.0031 6012 adpu320 (241c9e37f8ce45ef51c3de27515ca4e5) C:\Windows\system32\drivers\adpu320.sys
2011/06/16 21:40:48.0842 6012 AFD (763e172a55177e478cb419f88fd0ba03) C:\Windows\system32\drivers\afd.sys
2011/06/16 21:40:49.0201 6012 agp440 (13f9e33747e6b41a3ff305c37db0d360) C:\Windows\system32\drivers\agp440.sys
2011/06/16 21:40:49.0482 6012 aic78xx (ae1fdf7bf7bb6c6a70f67699d880592a) C:\Windows\system32\drivers\djsvs.sys
2011/06/16 21:40:49.0825 6012 aliide (9eaef5fc9b8e351afa7e78a6fae91f91) C:\Windows\system32\drivers\aliide.sys
2011/06/16 21:40:50.0028 6012 amdagp (c47344bc706e5f0b9dce369516661578) C:\Windows\system32\drivers\amdagp.sys
2011/06/16 21:40:50.0246 6012 amdide (9b78a39a4c173fdbc1321e0dd659b34c) C:\Windows\system32\drivers\amdide.sys
2011/06/16 21:40:50.0527 6012 AmdK7 (18f29b49ad23ecee3d2a826c725c8d48) C:\Windows\system32\drivers\amdk7.sys
2011/06/16 21:40:50.0854 6012 AmdK8 (93ae7f7dd54ab986a6f1a1b37be7442d) C:\Windows\system32\drivers\amdk8.sys
2011/06/16 21:40:51.0026 6012 arc (5d2888182fb46632511acee92fdad522) C:\Windows\system32\drivers\arc.sys
2011/06/16 21:40:51.0432 6012 arcsas (5e2a321bd7c8b3624e41fdec3e244945) C:\Windows\system32\drivers\arcsas.sys
2011/06/16 21:40:51.0900 6012 AsyncMac (53b202abee6455406254444303e87be1) C:\Windows\system32\DRIVERS\asyncmac.sys
2011/06/16 21:40:52.0383 6012 atapi (2d9c903dc76a66813d350a562de40ed9) C:\Windows\system32\drivers\atapi.sys
2011/06/16 21:40:52.0648 6012 Beep (67e506b75bd5326a3ec7b70bd014dfb6) C:\Windows\system32\drivers\Beep.sys
2011/06/16 21:40:52.0882 6012 blbdrive (d4df28447741fd3d953526e33a617397) C:\Windows\system32\drivers\blbdrive.sys
2011/06/16 21:40:53.0226 6012 bowser (8153396d5551276227fa146900f734e6) C:\Windows\system32\DRIVERS\bowser.sys
2011/06/16 21:40:53.0553 6012 BrFiltLo (9f9acc7f7ccde8a15c282d3f88b43309) C:\Windows\system32\drivers\brfiltlo.sys
2011/06/16 21:40:53.0787 6012 BrFiltUp (56801ad62213a41f6497f96dee83755a) C:\Windows\system32\drivers\brfiltup.sys
2011/06/16 21:40:54.0021 6012 Brserid (b304e75cff293029eddf094246747113) C:\Windows\system32\drivers\brserid.sys
2011/06/16 21:40:54.0208 6012 BrSerWdm (203f0b1e73adadbbb7b7b1fabd901f6b) C:\Windows\system32\drivers\brserwdm.sys
2011/06/16 21:40:54.0396 6012 BrUsbMdm (bd456606156ba17e60a04e18016ae54b) C:\Windows\system32\drivers\brusbmdm.sys
2011/06/16 21:40:54.0723 6012 BrUsbSer (af72ed54503f717a43268b3cc5faec2e) C:\Windows\system32\drivers\brusbser.sys
2011/06/16 21:40:54.0957 6012 BTHMODEM (ad07c1ec6665b8b35741ab91200c6b68) C:\Windows\system32\drivers\bthmodem.sys
2011/06/16 21:40:55.0191 6012 cdfs (7add03e75beb9e6dd102c3081d29840a) C:\Windows\system32\DRIVERS\cdfs.sys
2011/06/16 21:40:55.0410 6012 cdrom (1ec25cea0de6ac4718bf89f9e1778b57) C:\Windows\system32\DRIVERS\cdrom.sys
2011/06/16 21:40:55.0628 6012 circlass (e5d4133f37219dbcfe102bc61072589d) C:\Windows\system32\drivers\circlass.sys
2011/06/16 21:40:55.0815 6012 CLFS (465745561c832b29f7c48b488aab3842) C:\Windows\system32\CLFS.sys
2011/06/16 21:40:56.0112 6012 cmdide (0ca25e686a4928484e9fdabd168ab629) C:\Windows\system32\drivers\cmdide.sys
2011/06/16 21:40:56.0564 6012 Compbatt (6afef0b60fa25de07c0968983ee4f60a) C:\Windows\system32\drivers\compbatt.sys
2011/06/16 21:40:56.0876 6012 crcdisk (741e9dff4f42d2d8477d0fc1dc0df871) C:\Windows\system32\drivers\crcdisk.sys
2011/06/16 21:40:57.0094 6012 Crusoe (1f07becdca750766a96cda811ba86410) C:\Windows\system32\drivers\crusoe.sys
2011/06/16 21:40:57.0360 6012 DfsC (9e635ae5e8ad93e2b5989e2e23679f97) C:\Windows\system32\Drivers\dfsc.sys
2011/06/16 21:40:57.0672 6012 disk (64109e623abd6955c8fb110b592e68b7) C:\Windows\system32\drivers\disk.sys
2011/06/16 21:40:57.0952 6012 drmkaud (97fef831ab90bee128c9af390e243f80) C:\Windows\system32\drivers\drmkaud.sys
2011/06/16 21:40:58.0062 6012 DXGKrnl (85f33880b8cfb554bd3d9ccdb486845a) C:\Windows\System32\drivers\dxgkrnl.sys
2011/06/16 21:40:58.0545 6012 E1G60 (5425f74ac0c1dbd96a1e04f17d63f94c) C:\Windows\system32\DRIVERS\E1G60I32.sys
2011/06/16 21:40:58.0951 6012 Ecache (dd2cd259d83d8b72c02c5f2331ff9d68) C:\Windows\system32\drivers\ecache.sys
2011/06/16 21:40:59.0528 6012 elxstor (23b62471681a124889978f6295b3f4c6) C:\Windows\system32\drivers\elxstor.sys
2011/06/16 21:40:59.0949 6012 ErrDev (3db974f3935483555d7148663f726c61) C:\Windows\system32\drivers\errdev.sys
2011/06/16 21:41:00.0433 6012 exfat (0d858eb20589a34efb25695acaa6aa2d) C:\Windows\system32\drivers\exfat.sys
2011/06/16 21:41:00.0760 6012 fastfat (3c489390c2e2064563727752af8eab9e) C:\Windows\system32\drivers\fastfat.sys
2011/06/16 21:41:00.0948 6012 fdc (afe1e8b9782a0dd7fb46bbd88e43f89a) C:\Windows\system32\DRIVERS\fdc.sys
2011/06/16 21:41:01.0213 6012 FileInfo (a8c0139a884861e3aae9cfe73b208a9f) C:\Windows\system32\drivers\fileinfo.sys
2011/06/16 21:41:01.0462 6012 Filetrace (0ae429a696aecbc5970e3cf2c62635ae) C:\Windows\system32\drivers\filetrace.sys
2011/06/16 21:41:01.0681 6012 flpydisk (85b7cf99d532820495d68d747fda9ebd) C:\Windows\system32\DRIVERS\flpydisk.sys
2011/06/16 21:41:01.0837 6012 FltMgr (05ea53afe985443011e36dab07343b46) C:\Windows\system32\drivers\fltmgr.sys
2011/06/16 21:41:01.0946 6012 Fs_Rec (65ea8b77b5851854f0c55c43fa51a198) C:\Windows\system32\drivers\Fs_Rec.sys
2011/06/16 21:41:02.0024 6012 gagp30kx (34582a6e6573d54a07ece5fe24a126b5) C:\Windows\system32\drivers\gagp30kx.sys
2011/06/16 21:41:02.0508 6012 HdAudAddService (cb04c744be0a61b1d648faed182c3b59) C:\Windows\system32\drivers\HdAudio.sys
2011/06/16 21:41:02.0726 6012 HDAudBus (c87b1ee051c0464491c1a7b03fa0bc99) C:\Windows\system32\DRIVERS\HDAudBus.sys
2011/06/16 21:41:02.0944 6012 HidBth (1338520e78d90154ed6be8f84de5fceb) C:\Windows\system32\drivers\hidbth.sys
2011/06/16 21:41:03.0163 6012 HidIr (ff3160c3a2445128c5a6d9b076da519e) C:\Windows\system32\drivers\hidir.sys
2011/06/16 21:41:03.0646 6012 HidUsb (854ca287ab7faf949617a788306d967e) C:\Windows\system32\DRIVERS\hidusb.sys
2011/06/16 21:41:03.0943 6012 HpCISSs (16ee7b23a009e00d835cdb79574a91a6) C:\Windows\system32\drivers\hpcisss.sys
2011/06/16 21:41:04.0239 6012 HTTP (96e241624c71211a79c84f50a8e71cab) C:\Windows\system32\drivers\HTTP.sys
2011/06/16 21:41:04.0692 6012 i2omp (c6b032d69650985468160fc9937cf5b4) C:\Windows\system32\drivers\i2omp.sys
2011/06/16 21:41:05.0082 6012 i8042prt (22d56c8184586b7a1f6fa60be5f5a2bd) C:\Windows\system32\DRIVERS\i8042prt.sys
2011/06/16 21:41:05.0550 6012 iaStor (580bfec487c55264bfe3d60c3c24eee1) C:\Windows\system32\drivers\iastor.sys
2011/06/16 21:41:05.0955 6012 iaStorV (54155ea1b0df185878e0fc9ec3ac3a14) C:\Windows\system32\drivers\iastorv.sys
2011/06/16 21:41:06.0252 6012 iirsp (2d077bf86e843f901d8db709c95b49a5) C:\Windows\system32\drivers\iirsp.sys
2011/06/16 21:41:06.0408 6012 int15 (c6e5276c00ebdeb096bb5ef4b797d1b6) C:\Acer\Empowering Technology\eRecovery\int15.sys
2011/06/16 21:41:06.0735 6012 IntcAzAudAddService (4c01298060cf930d26a75a86b874b6ae) C:\Windows\system32\drivers\RTKVHDA.sys
2011/06/16 21:41:07.0437 6012 intelide (83aa759f3189e6370c30de5dc5590718) C:\Windows\system32\drivers\intelide.sys
2011/06/16 21:41:07.0734 6012 intelppm (224191001e78c89dfa78924c3ea595ff) C:\Windows\system32\DRIVERS\intelppm.sys
2011/06/16 21:41:08.0264 6012 IPMIDRV (b25aaf203552b7b3491139d582b39ad1) C:\Windows\system32\drivers\ipmidrv.sys
2011/06/16 21:41:08.0514 6012 IPNAT (8793643a67b42cec66490b2a0cf92d68) C:\Windows\system32\DRIVERS\ipnat.sys
2011/06/16 21:41:08.0763 6012 IRENUM (109c0dfb82c3632fbd11949b73aeeac9) C:\Windows\system32\drivers\irenum.sys
2011/06/16 21:41:09.0106 6012 isapnp (6c70698a3e5c4376c6ab5c7c17fb0614) C:\Windows\system32\drivers\isapnp.sys
2011/06/16 21:41:09.0387 6012 iScsiPrt (f247eec28317f6c739c16de420097301) C:\Windows\system32\DRIVERS\msiscsi.sys
2011/06/16 21:41:09.0793 6012 iteatapi (bced60d16156e428f8df8cf27b0df150) C:\Windows\system32\drivers\iteatapi.sys
2011/06/16 21:41:10.0058 6012 iteraid (06fa654504a498c30adca8bec4e87e7e) C:\Windows\system32\drivers\iteraid.sys
2011/06/16 21:41:10.0354 6012 kbdclass (37605e0a8cf00cbba538e753e4344c6e) C:\Windows\system32\DRIVERS\kbdclass.sys
2011/06/16 21:41:10.0542 6012 kbdhid (18247836959ba67e3511b62846b9c2e0) C:\Windows\system32\DRIVERS\kbdhid.sys
2011/06/16 21:41:10.0760 6012 KSecDD (7a0cf7908b6824d6a2a1d313e5ae3dca) C:\Windows\system32\Drivers\ksecdd.sys
2011/06/16 21:41:11.0462 6012 lltdio (d1c5883087a0c3f1344d9d55a44901f6) C:\Windows\system32\DRIVERS\lltdio.sys
2011/06/16 21:41:11.0680 6012 LSI_FC (c7e15e82879bf3235b559563d4185365) C:\Windows\system32\drivers\lsi_fc.sys
2011/06/16 21:41:12.0070 6012 LSI_SAS (ee01ebae8c9bf0fa072e0ff68718920a) C:\Windows\system32\drivers\lsi_sas.sys
2011/06/16 21:41:12.0507 6012 LSI_SCSI (912a04696e9ca30146a62afa1463dd5c) C:\Windows\system32\drivers\lsi_scsi.sys
2011/06/16 21:41:12.0882 6012 luafv (8f5c7426567798e62a3b3614965d62cc) C:\Windows\system32\drivers\luafv.sys
2011/06/16 21:41:13.0350 6012 megasas (0001ce609d66632fa17b84705f658879) C:\Windows\system32\drivers\megasas.sys
2011/06/16 21:41:13.0740 6012 MegaSR (c252f32cd9a49dbfc25ecf26ebd51a99) C:\Windows\system32\drivers\megasr.sys
2011/06/16 21:41:14.0176 6012 Modem (e13b5ea0f51ba5b1512ec671393d09ba) C:\Windows\system32\drivers\modem.sys
2011/06/16 21:41:14.0442 6012 monitor (0a9bb33b56e294f686abb7c1e4e2d8a8) C:\Windows\system32\DRIVERS\monitor.sys
2011/06/16 21:41:14.0722 6012 mouclass (5bf6a1326a335c5298477754a506d263) C:\Windows\system32\DRIVERS\mouclass.sys
2011/06/16 21:41:15.0081 6012 mouhid (93b8d4869e12cfbe663915502900876f) C:\Windows\system32\DRIVERS\mouhid.sys
2011/06/16 21:41:15.0409 6012 MountMgr (bdafc88aa6b92f7842416ea6a48e1600) C:\Windows\system32\drivers\mountmgr.sys
2011/06/16 21:41:15.0627 6012 mpio (511d011289755dd9f9a7579fb0b064e6) C:\Windows\system32\drivers\mpio.sys
2011/06/16 21:41:15.0970 6012 mpsdrv (22241feba9b2defa669c8cb0a8dd7d2e) C:\Windows\system32\drivers\mpsdrv.sys
2011/06/16 21:41:16.0470 6012 Mraid35x (4fbbb70d30fd20ec51f80061703b001e) C:\Windows\system32\drivers\mraid35x.sys
2011/06/16 21:41:16.0672 6012 MREMP50 (9bd4dcb5412921864a7aacdedfbd1923) C:\PROGRA~1\COMMON~1\Motive\MREMP50.SYS
2011/06/16 21:41:17.0000 6012 MRESP50 (07c02c892e8e1a72d6bf35004f0e9c5e) C:\PROGRA~1\COMMON~1\Motive\MRESP50.SYS
2011/06/16 21:41:17.0187 6012 MRxDAV (ae3de84536b6799d2267443cec8edbb9) C:\Windows\system32\drivers\mrxdav.sys
2011/06/16 21:41:17.0562 6012 mrxsmb (cc752d233ef39875ca6885d9415ba869) C:\Windows\system32\DRIVERS\mrxsmb.sys
2011/06/16 21:41:17.0796 6012 mrxsmb10 (9049dddd4bd27d43d82f5968f1da76e4) C:\Windows\system32\DRIVERS\mrxsmb10.sys
2011/06/16 21:41:18.0232 6012 mrxsmb20 (91dc069b6831ef564e7d8c97eaf0343e) C:\Windows\system32\DRIVERS\mrxsmb20.sys
2011/06/16 21:41:18.0451 6012 msahci (28023e86f17001f7cd9b15a5bc9ae07d) C:\Windows\system32\drivers\msahci.sys
2011/06/16 21:41:18.0888 6012 msdsm (4468b0f385a86ecddaf8d3ca662ec0e7) C:\Windows\system32\drivers\msdsm.sys
2011/06/16 21:41:19.0200 6012 Msfs (a9927f4a46b816c92f461acb90cf8515) C:\Windows\system32\drivers\Msfs.sys
2011/06/16 21:41:19.0293 6012 msisadrv (0f400e306f385c56317357d6dea56f62) C:\Windows\system32\drivers\msisadrv.sys
2011/06/16 21:41:19.0480 6012 MSKSSRV (d8c63d34d9c9e56c059e24ec7185cc07) C:\Windows\system32\drivers\MSKSSRV.sys
2011/06/16 21:41:19.0683 6012 MSPCLOCK (1d373c90d62ddb641d50e55b9e78d65e) C:\Windows\system32\drivers\MSPCLOCK.sys
2011/06/16 21:41:19.0933 6012 MSPQM (b572da05bf4e098d4bba3a4734fb505b) C:\Windows\system32\drivers\MSPQM.sys
2011/06/16 21:41:20.0494 6012 MsRPC (b5614aecb05a9340aa0fb55bf561cc63) C:\Windows\system32\drivers\MsRPC.sys
2011/06/16 21:41:20.0806 6012 mssmbios (e384487cb84be41d09711c30ca79646c) C:\Windows\system32\DRIVERS\mssmbios.sys
2011/06/16 21:41:20.0962 6012 MSTEE (7199c1eec1e4993caf96b8c0a26bd58a) C:\Windows\system32\drivers\MSTEE.sys
2011/06/16 21:41:21.0352 6012 Mup (6dfd1d322de55b0b7db7d21b90bec49c) C:\Windows\system32\Drivers\mup.sys
2011/06/16 21:41:21.0586 6012 NativeWifiP (3c21ce48ff529bb73dadb98770b54025) C:\Windows\system32\DRIVERS\nwifi.sys
2011/06/16 21:41:21.0789 6012 NDIS (9bdc71790fa08f0a0b5f10462b1bd0b1) C:\Windows\system32\drivers\ndis.sys
2011/06/16 21:41:22.0195 6012 NdisTapi (0e186e90404980569fb449ba7519ae61) C:\Windows\system32\DRIVERS\ndistapi.sys
2011/06/16 21:41:22.0522 6012 Ndisuio (d6973aa34c4d5d76c0430b181c3cd389) C:\Windows\system32\DRIVERS\ndisuio.sys
2011/06/16 21:41:22.0788 6012 NdisWan (3d14c3b3496f88890d431e8aa022a411) C:\Windows\system32\DRIVERS\ndiswan.sys
2011/06/16 21:41:22.0959 6012 NDProxy (71dab552b41936358f3b541ae5997fb3) C:\Windows\system32\drivers\NDProxy.sys
2011/06/16 21:41:23.0240 6012 NetBIOS (bcd093a5a6777cf626434568dc7dba78) C:\Windows\system32\DRIVERS\netbios.sys
2011/06/16 21:41:23.0458 6012 netbt (7c5fee5b1c5728507cd96fb4a13e7a02) C:\Windows\system32\DRIVERS\netbt.sys
2011/06/16 21:41:23.0739 6012 nfrd960 (2e7fb731d4790a1bc6270accefacb36e) C:\Windows\system32\drivers\nfrd960.sys
2011/06/16 21:41:23.0926 6012 Npfs (ecb5003f484f9ed6c608d6d6c7886cbb) C:\Windows\system32\drivers\Npfs.sys
2011/06/16 21:41:24.0129 6012 nsiproxy (609773e344a97410ce4ebf74a8914fcf) C:\Windows\system32\drivers\nsiproxy.sys
2011/06/16 21:41:24.0363 6012 Ntfs (b4effe29eb4f15538fd8a9681108492d) C:\Windows\system32\drivers\Ntfs.sys
2011/06/16 21:41:24.0582 6012 NTIDrvr (7f1c1f78d709c4a54cbb46ede7e0b48d) C:\Windows\system32\DRIVERS\NTIDrvr.sys
2011/06/16 21:41:24.0784 6012 ntrigdigi (e875c093aec0c978a90f30c9e0dfbb72) C:\Windows\system32\drivers\ntrigdigi.sys
2011/06/16 21:41:25.0003 6012 Null (c5dbbcda07d780bda9b685df333bb41e) C:\Windows\system32\drivers\Null.sys
2011/06/16 21:41:25.0206 6012 NVENETFD (b896fb556b4dc1e1d2943559ea79c5c5) C:\Windows\system32\DRIVERS\nvmfdx32.sys
2011/06/16 21:41:25.0502 6012 NVHDA (f3ef6cb754c908c5e79fe5bb4a7e39ba) C:\Windows\system32\drivers\nvhda32v.sys
2011/06/16 21:41:26.0079 6012 nvlddmkm (ff58c7a7da6116c1f71e883cb088d598) C:\Windows\system32\DRIVERS\nvlddmkm.sys
2011/06/16 21:41:26.0578 6012 nvraid (2edf9e7751554b42cbb60116de727101) C:\Windows\system32\drivers\nvraid.sys
2011/06/16 21:41:26.0797 6012 nvrd32 (6934105ecc6a19570160d794e301e595) C:\Windows\system32\drivers\nvrd32.sys
2011/06/16 21:41:27.0015 6012 nvsmu (7ec12a73067baca25a8e3e2a58ae83d8) C:\Windows\system32\DRIVERS\nvsmu.sys
2011/06/16 21:41:27.0156 6012 nvstor (abed0c09758d1d97db0042dbb2688177) C:\Windows\system32\drivers\nvstor.sys
2011/06/16 21:41:27.0265 6012 nvstor32 (d7b213299852d2026dbc90dab77ef06c) C:\Windows\system32\drivers\nvstor32.sys
2011/06/16 21:41:27.0499 6012 nv_agp (18bbdf913916b71bd54575bdb6eeac0b) C:\Windows\system32\drivers\nv_agp.sys
2011/06/16 21:41:27.0811 6012 ohci1394 (790e27c3db53410b40ff9ef2fd10a1d9) C:\Windows\system32\DRIVERS\ohci1394.sys
2011/06/16 21:41:28.0014 6012 Parport (0fa9b5055484649d63c303fe404e5f4d) C:\Windows\system32\drivers\parport.sys
2011/06/16 21:41:28.0232 6012 partmgr (3b38467e7c3daed009dfe359e17f139f) C:\Windows\system32\drivers\partmgr.sys
2011/06/16 21:41:28.0435 6012 Parvdm (4f9a6a8a31413180d0fcb279ad5d8112) C:\Windows\system32\drivers\parvdm.sys
2011/06/16 21:41:28.0669 6012 pci (01b94418deb235dff777cc80076354b4) C:\Windows\system32\drivers\pci.sys
2011/06/16 21:41:28.0887 6012 pciide (fc175f5ddab666d7f4d17449a547626f) C:\Windows\system32\drivers\pciide.sys
2011/06/16 21:41:29.0012 6012 pcmcia (e6f3fb1b86aa519e7698ad05e58b04e5) C:\Windows\system32\drivers\pcmcia.sys
2011/06/16 21:41:29.0355 6012 PEAUTH (6349f6ed9c623b44b52ea3c63c831a92) C:\Windows\system32\drivers\peauth.sys
2011/06/16 21:41:29.0652 6012 PptpMiniport (ecfffaec0c1ecd8dbc77f39070ea1db1) C:\Windows\system32\DRIVERS\raspptp.sys
2011/06/16 21:41:29.0854 6012 Processor (2027293619dd0f047c584cf2e7df4ffd) C:\Windows\system32\drivers\processr.sys
2011/06/16 21:41:30.0120 6012 PSched (bfef604508a0ed1eae2a73e872555ffb) C:\Windows\system32\DRIVERS\pacer.sys
2011/06/16 21:41:30.0354 6012 PSDFilter (ab94285ff6c6bc5433407d8d182a4bb4) C:\Windows\system32\DRIVERS\psdfilter.sys
2011/06/16 21:41:30.0463 6012 PSDNServ (2aaf9a5d7a63d26bfaea853c5f2292bc) C:\Windows\system32\DRIVERS\PSDNServ.sys
2011/06/16 21:41:30.0556 6012 psdvdisk (0eb8cec99855beae5b0d02c2302619ef) C:\Windows\system32\DRIVERS\PSDVdisk.sys
2011/06/16 21:41:30.0915 6012 ql2300 (0a6db55afb7820c99aa1f3a1d270f4f6) C:\Windows\system32\drivers\ql2300.sys
2011/06/16 21:41:31.0165 6012 ql40xx (81a7e5c076e59995d54bc1ed3a16e60b) C:\Windows\system32\drivers\ql40xx.sys
2011/06/16 21:41:31.0414 6012 QWAVEdrv (9f5e0e1926014d17486901c88eca2db7) C:\Windows\system32\drivers\qwavedrv.sys
2011/06/16 21:41:31.0664 6012 RasAcd (147d7f9c556d259924351feb0de606c3) C:\Windows\system32\DRIVERS\rasacd.sys
2011/06/16 21:41:32.0070 6012 Rasl2tp (a214adbaf4cb47dd2728859ef31f26b0) C:\Windows\system32\DRIVERS\rasl2tp.sys
2011/06/16 21:41:32.0350 6012 RasPppoe (3e9d9b048107b40d87b97df2e48e0744) C:\Windows\system32\DRIVERS\raspppoe.sys
2011/06/16 21:41:32.0631 6012 RasSstp (a7d141684e9500ac928a772ed8e6b671) C:\Windows\system32\DRIVERS\rassstp.sys
2011/06/16 21:41:32.0865 6012 rdbss (6e1c5d0457622f9ee35f683110e93d14) C:\Windows\system32\DRIVERS\rdbss.sys
2011/06/16 21:41:33.0068 6012 RDPCDD (89e59be9a564262a3fb6c4f4f1cd9899) C:\Windows\system32\DRIVERS\RDPCDD.sys
2011/06/16 21:41:33.0364 6012 rdpdr (fbc0bacd9c3d7f6956853f64a66e252d) C:\Windows\system32\drivers\rdpdr.sys
2011/06/16 21:41:33.0567 6012 RDPENCDD (9d91fe5286f748862ecffa05f8a0710c) C:\Windows\system32\drivers\rdpencdd.sys
2011/06/16 21:41:33.0754 6012 RDPWD (e1c18f4097a5abcec941dc4b2f99db7e) C:\Windows\system32\drivers\RDPWD.sys
2011/06/16 21:41:34.0020 6012 rspndr (9c508f4074a39e8b4b31d27198146fad) C:\Windows\system32\DRIVERS\rspndr.sys
2011/06/16 21:41:34.0363 6012 sbp2port (3ce8f073a557e172b330109436984e30) C:\Windows\system32\drivers\sbp2port.sys
2011/06/16 21:41:34.0628 6012 secdrv (90a3935d05b494a5a39d37e71f09a677) C:\Windows\system32\drivers\secdrv.sys
2011/06/16 21:41:34.0878 6012 Serenum (ce9ec966638ef0b10b864ddedf62a099) C:\Windows\system32\DRIVERS\serenum.sys
2011/06/16 21:41:35.0065 6012 Serial (6d663022db3e7058907784ae14b69898) C:\Windows\system32\DRIVERS\serial.sys
2011/06/16 21:41:35.0283 6012 sermouse (8af3d28a879bf75db53a0ee7a4289624) C:\Windows\system32\drivers\sermouse.sys
2011/06/16 21:41:35.0533 6012 sffdisk (3efa810bdca87f6ecc24f9832243fe86) C:\Windows\system32\drivers\sffdisk.sys
2011/06/16 21:41:35.0767 6012 sffp_mmc (e95d451f7ea3e583aec75f3b3ee42dc5) C:\Windows\system32\drivers\sffp_mmc.sys
2011/06/16 21:41:35.0938 6012 sffp_sd (3d0ea348784b7ac9ea9bd9f317980979) C:\Windows\system32\drivers\sffp_sd.sys
2011/06/16 21:41:36.0079 6012 sfloppy (46ed8e91793b2e6f848015445a0ac188) C:\Windows\system32\drivers\sfloppy.sys
2011/06/16 21:41:36.0188 6012 sisagp (1d76624a09a054f682d746b924e2dbc3) C:\Windows\system32\drivers\sisagp.sys
2011/06/16 21:41:36.0297 6012 SiSRaid2 (43cb7aa756c7db280d01da9b676cfde2) C:\Windows\system32\drivers\sisraid2.sys
2011/06/16 21:41:36.0469 6012 SiSRaid4 (a99c6c8b0baa970d8aa59ddc50b57f94) C:\Windows\system32\drivers\sisraid4.sys
2011/06/16 21:41:36.0734 6012 Smb (031e6bcd53c9b2b9ace111eafec347b6) C:\Windows\system32\DRIVERS\smb.sys
2011/06/16 21:41:37.0030 6012 spldr (7aebdeef071fe28b0eef2cdd69102bff) C:\Windows\system32\drivers\spldr.sys
2011/06/16 21:41:37.0296 6012 srv (2252aef839b1093d16761189f45af885) C:\Windows\system32\DRIVERS\srv.sys
2011/06/16 21:41:37.0498 6012 srv2 (96512f4a30b741e7d33a7936b9abbc20) C:\Windows\system32\DRIVERS\srv2.sys
2011/06/16 21:41:37.0717 6012 srvnet (1c69e33e0e23626da5a34ca5ba0dd990) C:\Windows\system32\DRIVERS\srvnet.sys
2011/06/16 21:41:37.0920 6012 swenum (7ba58ecf0c0a9a69d44b3dca62becf56) C:\Windows\system32\DRIVERS\swenum.sys
2011/06/16 21:41:38.0138 6012 Symc8xx (192aa3ac01df071b541094f251deed10) C:\Windows\system32\drivers\symc8xx.sys
2011/06/16 21:41:38.0497 6012 Sym_hi (8c8eb8c76736ebaf3b13b633b2e64125) C:\Windows\system32\drivers\sym_hi.sys
2011/06/16 21:41:38.0684 6012 Sym_u3 (8072af52b5fd103bbba387a1e49f62cb) C:\Windows\system32\drivers\sym_u3.sys
2011/06/16 21:41:39.0027 6012 Tcpip (782568ab6a43160a159b6215b70bcce9) C:\Windows\system32\drivers\tcpip.sys
2011/06/16 21:41:39.0823 6012 Tcpip6 (782568ab6a43160a159b6215b70bcce9) C:\Windows\system32\DRIVERS\tcpip.sys
2011/06/16 21:41:40.0072 6012 tcpipreg (d4a2e4a4b011f3a883af77315a5ae76b) C:\Windows\system32\drivers\tcpipreg.sys
2011/06/16 21:41:40.0260 6012 TDPIPE (5dcf5e267be67a1ae926f2df77fbcc56) C:\Windows\system32\drivers\tdpipe.sys
2011/06/16 21:41:40.0447 6012 TDTCP (389c63e32b3cefed425b61ed92d3f021) C:\Windows\system32\drivers\tdtcp.sys
2011/06/16 21:41:40.0618 6012 tdx (d09276b1fab033ce1d40dcbdf303d10f) C:\Windows\system32\DRIVERS\tdx.sys
2011/06/16 21:41:40.0743 6012 TermDD (a048056f5e1a96a9bf3071b91741a5aa) C:\Windows\system32\DRIVERS\termdd.sys
2011/06/16 21:41:41.0071 6012 tssecsrv (dcf0f056a2e4f52287264f5ab29cf206) C:\Windows\system32\DRIVERS\tssecsrv.sys
2011/06/16 21:41:41.0664 6012 tunmp (caecc0120ac49e3d2f758b9169872d38) C:\Windows\system32\DRIVERS\tunmp.sys
2011/06/16 21:41:41.0944 6012 tunnel (6042505ff6fa9ac1ef7684d0e03b6940) C:\Windows\system32\DRIVERS\tunnel.sys
2011/06/16 21:41:42.0116 6012 tvicport (97dd70feca64fb4f63de7bb7e66a80b1) C:\Windows\system32\drivers\tvicport.sys
2011/06/16 21:41:42.0350 6012 uagp35 (7d33c4db2ce363c8518d2dfcf533941f) C:\Windows\system32\drivers\uagp35.sys
2011/06/16 21:41:42.0490 6012 udfs (8b5088058fa1d1cd897a2113ccff6c58) C:\Windows\system32\DRIVERS\udfs.sys
2011/06/16 21:41:42.0709 6012 uliagpkx (b0acfdc9e4af279e9116c03e014b2b27) C:\Windows\system32\drivers\uliagpkx.sys
2011/06/16 21:41:42.0943 6012 uliahci (9224bb254f591de4ca8d572a5f0d635c) C:\Windows\system32\drivers\uliahci.sys
2011/06/16 21:41:43.0146 6012 UlSata (8514d0e5cd0534467c5fc61be94a569f) C:\Windows\system32\drivers\ulsata.sys
2011/06/16 21:41:43.0333 6012 ulsata2 (38c3c6e62b157a6bc46594fada45c62b) C:\Windows\system32\drivers\ulsata2.sys
2011/06/16 21:41:43.0629 6012 umbus (32cff9f809ae9aed85464492bf3e32d2) C:\Windows\system32\DRIVERS\umbus.sys
2011/06/16 21:41:43.0801 6012 usbccgp (caf811ae4c147ffcd5b51750c7f09142) C:\Windows\system32\DRIVERS\usbccgp.sys
2011/06/16 21:41:43.0941 6012 usbcir (e9476e6c486e76bc4898074768fb7131) C:\Windows\system32\drivers\usbcir.sys
2011/06/16 21:41:44.0035 6012 usbehci (cebe90821810e76320155beba722fcf9) C:\Windows\system32\DRIVERS\usbehci.sys
2011/06/16 21:41:44.0206 6012 usbhub (cc6b28e4ce39951357963119ce47b143) C:\Windows\system32\DRIVERS\usbhub.sys
2011/06/16 21:41:44.0394 6012 usbohci (7bdb7b0e7d45ac0402d78b90789ef47c) C:\Windows\system32\DRIVERS\usbohci.sys
2011/06/16 21:41:44.0596 6012 usbprint (b51e52acf758be00ef3a58ea452fe360) C:\Windows\system32\drivers\usbprint.sys
2011/06/16 21:41:44.0815 6012 USBSTOR (87ba6b83c5d19b69160968d07d6e2982) C:\Windows\system32\DRIVERS\USBSTOR.SYS
2011/06/16 21:41:45.0096 6012 usbuhci (814d653efc4d48be3b04a307eceff56f) C:\Windows\system32\DRIVERS\usbuhci.sys
2011/06/16 21:41:45.0408 6012 vga (87b06e1f30b749a114f74622d013f8d4) C:\Windows\system32\DRIVERS\vgapnp.sys
2011/06/16 21:41:45.0579 6012 VgaSave (2e93ac0a1d8c79d019db6c51f036636c) C:\Windows\System32\drivers\vga.sys
2011/06/16 21:41:45.0782 6012 viaagp (5d7159def58a800d5781ba3a879627bc) C:\Windows\system32\drivers\viaagp.sys
2011/06/16 21:41:45.0969 6012 ViaC7 (c4f3a691b5bad343e6249bd8c2d45dee) C:\Windows\system32\drivers\viac7.sys
2011/06/16 21:41:46.0234 6012 viaide (aadf5587a4063f52c2c3fed7887426fc) C:\Windows\system32\drivers\viaide.sys
2011/06/16 21:41:46.0578 6012 volmgr (69503668ac66c77c6cd7af86fbdf8c43) C:\Windows\system32\drivers\volmgr.sys
2011/06/16 21:41:46.0796 6012 volmgrx (98f5ffe6316bd74e9e2c97206c190196) C:\Windows\system32\drivers\volmgrx.sys
2011/06/16 21:41:47.0077 6012 volsnap (0b91f93264b06ee3fceba84ef4676995) C:\Windows\system32\drivers\volsnap.sys
2011/06/16 21:41:47.0092 6012 Suspicious file (Forged): C:\Windows\system32\drivers\volsnap.sys. Real md5: 0b91f93264b06ee3fceba84ef4676995, Fake md5: d8b4a53dd2769f226b3eb374374987c9
2011/06/16 21:41:47.0108 6012 volsnap - detected Rootkit.Win32.TDSS.tdl3 (0)
2011/06/16 21:41:47.0451 6012 vsmraid (587253e09325e6bf226b299774b728a9) C:\Windows\system32\drivers\vsmraid.sys
2011/06/16 21:41:47.0935 6012 WacomPen (48dfee8f1af7c8235d4e626f0c4fe031) C:\Windows\system32\drivers\wacompen.sys
2011/06/16 21:41:48.0231 6012 Wanarp (55201897378cca7af8b5efd874374a26) C:\Windows\system32\DRIVERS\wanarp.sys
2011/06/16 21:41:48.0278 6012 Wanarpv6 (55201897378cca7af8b5efd874374a26) C:\Windows\system32\DRIVERS\wanarp.sys
2011/06/16 21:41:48.0621 6012 Wd (78fe9542363f297b18c027b2d7e7c07f) C:\Windows\system32\drivers\wd.sys
2011/06/16 21:41:48.0902 6012 Wdf01000 (b6f0a7ad6d4bd325fbcd8bac96cd8d96) C:\Windows\system32\drivers\Wdf01000.sys
2011/06/16 21:41:49.0245 6012 WmiAcpi (2e7255d172df0b8283cdfb7b433b864e) C:\Windows\system32\DRIVERS\wmiacpi.sys
2011/06/16 21:41:49.0542 6012 WpdUsb (0cec23084b51b8288099eb710224e955) C:\Windows\system32\DRIVERS\wpdusb.sys
2011/06/16 21:41:49.0822 6012 ws2ifsl (e3a3cb253c0ec2494d4a61f5e43a389c) C:\Windows\system32\drivers\ws2ifsl.sys
2011/06/16 21:41:50.0166 6012 WUDFRd (ac13cb789d93412106b0fb6c7eb2bcb6) C:\Windows\system32\DRIVERS\WUDFRd.sys
2011/06/16 21:41:50.0415 6012 zntport (40ac8590cc9006dbb99ffcb37879d4c6) C:\Windows\system32\drivers\zntport.sys
2011/06/16 21:41:50.0493 6012 MBR (0x1B8) (a863475757cc50891aa8458c415e4b25) \Device\Harddisk0\DR0
2011/06/16 21:41:50.0680 6012 ================================================================================
2011/06/16 21:41:50.0680 6012 Scan finished
2011/06/16 21:41:50.0680 6012 ================================================================================
2011/06/16 21:41:50.0727 6004 Detected object count: 1
2011/06/16 21:41:50.0727 6004 Actual detected object count: 1
2011/06/16 21:43:01.0567 6004 volsnap (0b91f93264b06ee3fceba84ef4676995) C:\Windows\system32\drivers\volsnap.sys
2011/06/16 21:43:01.0645 6004 Suspicious file (Forged): C:\Windows\system32\drivers\volsnap.sys. Real md5: 0b91f93264b06ee3fceba84ef4676995, Fake md5: d8b4a53dd2769f226b3eb374374987c9
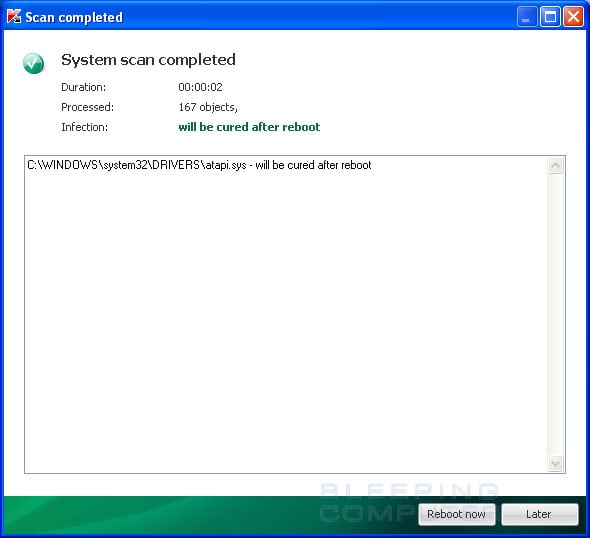
2011/06/16 21:43:13.0126 6004 Backup copy found, using it..
2011/06/16 21:43:13.0282 6004 C:\Windows\system32\drivers\volsnap.sys - will be cured after reboot
2011/06/16 21:43:13.0282 6004 Rootkit.Win32.TDSS.tdl3(volsnap) - User select action: Cure
2011/06/16 21:43:33.0812 5676 Deinitialize success
I'll do the combofix now, back shortly.